ALTE DOCUMENTE
|
||||||||||
Intel AMT Switchbox guide
Last updated: September 24, 2007
Table of Contents
Redirections (Telnet SOL, Local IDER, Passthru SOL & IDER):
Logging & Intel AMT Interceptor:
File Downloader & Disk Images:
How to setup Switchbox on a Linksys router?
How to configure Switchbox in TLS mode with a Correct Certificate?
How to perform Local IDER on a Unix based system?
Intel AMT Switchbox guide
Intel AMT Switchbox is a Software Tool that connects to and manages Intel AMT machines on a network. It is built in C and runs on Windows, UNIX and MIPS platforms (Routers). An IAMT management console like Intel AMT Commander or a Web Browser (Internet Explorer 7 and 6, Firefox 2.0 and 1.5) or Telnet can connect to Intel AMT Switchbox in TLS or non-TLS mode, authenticate once, and manage all of the Intel AMT machines that are under the control of this Switchbox.
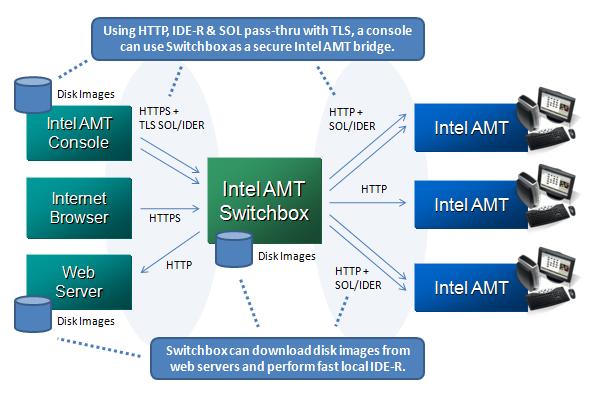
Working of Switchbox
These are the list of features, one can access while accessing switchbox from a browser:
This shows the current status and details of Switchbox like:
This allows add/delete switchbox users with different access-rights.
This feature allows a user to manage/control a list of Intel AMT machines on a network.
This feature is used to discover the Intel AMT machines in a sub-network specified by an IP range. Once Network Discovery is started, user can perform other tasks while the Network Discovery runs in background. User can directly add the computers discovered to the Manage Computers list by clicking on the computer hostnames/ips discovered.
Switchbox facilitates Telnet SOL, Local IDE-Redirection with a locally stored cdrom and floppy image and Pass-through SOL & IDER from a Console machine running Intel AMT Commander.
To Telnet SOL to Switchbox, a user should telnet to port 16990 or the TelnetRedirectPort value in switchbox.config. Once connected, user will be asked switchbox-username, switchbox-password and the AMT ID to which he wants to SOL/IDER to.
To enable Local IDER, we use a compile time flag. To do Local IDER to an AMT system, a user should goto Switchbox's Managed Computer webpage for that AMT system, select the images from the dropdowns and start IDER. A user can stop the redirection sessions on the same page by clicking on the trash icons for that sessions. Currently, the pre-built linux and mips executable do not have Local IDER enabled, since .iso files cannot be IDER properly on unix-based systems.
Switchbox logs all the important events in events.log file. These log file can also be viewed in Switchbox webpage under Event Log link. Old entries from the Log are flushed automatically when it reaches a pre-set threshold size. Alternatively, user is allowed to delete this log. User can also enable/disable logging to save space by setting the EventsLog key in switchbox.config.
Switchbox also can send various types of debug messages over a telnet session. You can telnet to Switchbox using Intel AMT Interceptor to the TelnetSOL port, set the debug message types you will like to receive and hit connect.
This cool feature can intercept all the HTTP requests/responses including SOAP requests/responses, SOL/IDER messages and other helpful debug trace messages.
This feature allows a user to upload images (floppy image or cdrom iso) on switchbox for redirection purpose. Switchbox has its own little file-downloader which can download an image from a web-link (this downloader does not work via a proxy server or from links that require authentication). A user can enter the link and the name it wants to give the file and select the type of redirection image.
This feature is disabled if Local IDER is disabled in switchbox.config.
Switchbox monitors the power-state of its managed computers periodically and maintains the power-state history for each machine for last 7 days.
To operate Switchbox in TLS mode, a Server-side Certificate needs to be configured in Switchbox. We have explained more on Certificate configuration in the Appendix section: "How to configure Switchbox in TLS mode with a Correct Certificate?"
Enter the AMT ID in the username field prompted for the Switchbox login as follows:
and the user will be connected to that Intel AMT Machine directly.
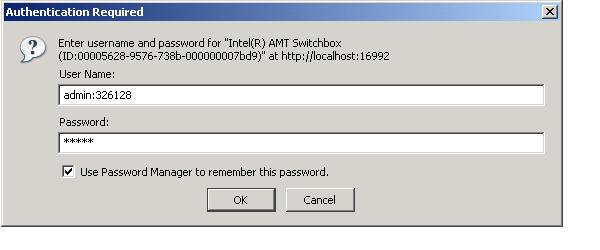
Using the same way, if a user connects directly to an Intel AMT Machine through Intel AMT Commander, then he can perform and SOL and IDE-R similar to how he can perform it directly using Intel AMT Commander.
Intel AMT Switchbox can be used in a
home,
switchbox.config:
To configure Intel AMT Switchbox
Sample file:
# This is a comment
# Port on which Intel AMT Switchbox accepts connections
# Note that if Switchbox is in TLS mode, the https server will run on
#Port + 1, i.e. in the following case, the https server will run on port 16993
Port=16992
# Intel AMT Switchbox unique ID
UUID=00005628-9576-738b-000000007bd9
#
RedirectPort=16994
#
TelnetSOLPort=16990
#To disable/enable logging
Logging=1
# admin password
user.admin=<admin-password>
# Additional users
user.<username1>=<password1>
user.<username2>=<password2>
user.<username3>=<password3>
#ImageLocation is the absolute directory path, where images for Local IDER are stored
ImageLocation=c work\PublicRelease\images\
mappings.txt:
Each line in this file of the below format represents data about a managed AMT computer:
<amt-unique-id>:<amt hostname/ip>:<amt username>:<amt password>:<desc>:<Everything here onwards is related to power-history for that system and is generated by Switchbox>
eg
556051:amtmachine.switchbox.intel.com:16992:admin:intelAMT@123:Intel(R) Active Management Technology 2.0.5:0:1190648479:4:
If you are adding an entry manually into this file, you need to enter only till the <desc> part, i.e. if you were to add the above e.g. manually then you shall only add
556051:amtmachine.switchbox.intel.com:16992:admin:intelAMT@123:Intel(R) Active Management Technology 2.0.5
redirectimages.txt: To store the names of the floppy and cdrom images for Local IDER. These images should be in the 'ImageLocation' directory configured in switchbox.config.
Entries are of format:
<Image-type - floppy/cdrom><-><image-name><-><image-desc>
e.g. floppy:fmsdos.img:Basic floppy image
https://192.168.4.3:16992 or https://192.168.4.3:16993
https://192.168.4.3:16992/getmappings
https://192.168.4.3:16992/addmapping?326128=192.168.5.80:16992:admin:intelAMT@123:Intel(R) Active Management Technology 2.1.0
https://192.168.4.3:16992/deletemapping?326128
https://192.168.4.3:16992/getinfo
https://192.168.4.3:16992/getusers
https://192.168.4.3:16992/adduser?guest=pass1234
https://192.168.4.3:16992/deleteuser?guest
https://192.168.4.3:16992/ netdiscstart?start=192.168.5.80&end=192.168.5.90
https://192.168.4.3:16992/netdiscstop
https://192.168.4.3:16992/netdiscinfo
https://192.168.4.3:16992/geteventlog
https://192.168.4.3:16992/deleteeventlog
https://192.168.4.3:16992/getredirections
https://192.168.4.3:16992/startlocalredirection?amtID=<AMT-ID>&floppy=<image-name>&cdrom=<image-name>
https://192.168.4.3:16992/stopredirection? <AMT-ID>:<Redirection-type>
https://192.168.4.3:16992/getimages
https://192.168.4.3:16993/getpower
"switchbox_mips" in the "Intel AMT Switchbox" folder is the binary for MIPS (Linksys router).
We are using Linksys WRTSL54GS ver 1.1 to run switchbox, since it provides good amount of RAM and disk space and USB support (you can plugin USB drive of 1GB for additional space) compared to other Linksys versions.
To configure the Router, connect your PC to any LAN ports of the router.
We flashed the router with the firmware "dd-wrt.v23_nokaid_generic.bin" since it allows SSH service. Default username/password for this firmware is root/admin for SSH and web-access. If it does not work, hard-reset the router once and try it again.
After flashing with the new firmware,
o Goto Router homepage Administration Services; Turn on the sshd service. "Save settings" at the bottom of the page.
o Goto the Router homepage Administration Management; Under JFFS2 support, enable JFFS2 and enable "Clean JFFS2". Then, hit "Save settings" at the bottom of the page. This should clean and format the JFFS2 (user-modifiable disk space) on router.
You can now SSH to the router with username= "root" and password = "admin", using a SSH client like putty
Copy the "Intel AMT Switchbox" folder to /jffs directory on the router; using SCP with a tool like WinSCP. Since the folder also contains some .exe, .dll and similar non-MIPS files related to windows platform, delete them before copying to router to save space. Also delete the .iso and .img files, since the router does not support Local Redirect currently.
To start the switchbox automatically whenever the router starts, create a file /jffs/etc/config/switchbox.startup (make sure you run chmod +x switchbox.startup) with the following lines
bin/sh
cd /jffs/Intel\ AMT\ Switchbox/
switchbox_mips &
Alternatively you can goto router's webpage Administration Commands
Enter the above 3 lines in the text-area and click "Save Startup"
Reboot the router. Enjoy your Switchbox!
By default, Switchbox is in TLS mode. To access its homepage, type
https://<switchbox-ip OR hostname>:16993
o To run Switchbox in non-TLS mode: Configure the 'Port' in Switchbox.config as 16992
https://<switchbox-ip OR hostname>:16992
When you install Switchbox for the 1st time and configure it to use TLS mode, it's certificate cannot be verified by Commander or other Consoles connecting to it since its Certificate Authority is not trusted and also since the Switchbox default certificate bears the hostname "127.0.0.1", which is not what the Consoles use to connect to Switchbox. When the Switchbox certificate cannot be verified by the Consoles, a red circular icon appears on switchbox IP to indicate this error. In case of Commander, it also disables the "Take Control" option, when you connect to any of the Managed AMT machines under Switchbox; for security purpose.
To configure a Switchbox with a proper certificate, the console machine needs to have a trusted root certificate and have Intel AMT Commander issue a new certificate to Switchbox using this trusted root certificate.
To generate a trusted root certificate on the Console machine using Intel AMT Director, please follow these steps:
o Open Intel AMT Director
o Click on "Certificate Manager" option.
o Click on "Create Root Certificate" button: here you can give a "Common name" and "Organization name" of your choice and make sure that the checkbox for "After creation, make this a trusted certificate" is enabled.
o Click "Generate. You will get a Security warning about "Do you want to install this certificate? click Yes.
o Close Director.
Now to issue a new certificate to Switchbox using Intel AMT Commander, follow these steps:
o Open Commander
o Connect to Switchbox; make sure that the red circular icon is still there on switchbox IP.
o Click on Settings tab on the right side panel
o Click on the 'x' button next to the 127.0.0.1 hostname.
o From the dropdown of Issuer Certificate, select the root certificate that you just generated using Director. Select the Key size.
o And click on OK.
o This will upload a new certificate on Switchbox and will reset the Connection in Commander.
o Connect to Switchbox after 5 seconds; you should now see a blue icon in place of the red circular icon (showing that the Switchbox Certificate can now be verified) and should also be able to "Take Control" of your AMT machines under Switchbox now.
You can use the same root certificate to issue certificates to many Switchboxes.
In Switchbox, a compile-time flag "LOCAL_REDIRECT_ENABLED" is set to enable Local IDER. We have kept it as a compile-time option since, on Unix based systems, enabling it also requires dynamically linking with libssl, libcrypto and libstdc++, which are not available by default on some embedded systems and also statically linking with Intel AMT Redirection Library (imrsdk), which is not available for all systems.
Once switchbox is built, the .iso file and the .img file which a user wants to use for Local IDER purpose has to be mounted to some directory on the system (Note that this is a requirement of the Intel AMT Redirection Library that we use for Local Redirection in Switchbox) as:
mount -o loop sample.iso /mnt/cdrom
mount -o loop sample.img /mnt/floppy
Make sure, there is an entry in redirectionimages.txt for these images. Then select these images on the Managed Computer webpage for that system and Start Local IDER.
|