Live Response Data Collection Lab
It is a hidden directory, it hides the directory created, and it is always on. It is uncommon and it is an administrative share.
2. Piracy of software, and open shari 323d37d ng of software.
Installed services running, access to non-common places such as different port. Sending stuff from a computer that would normally not be sent. Detection of additional software that might have been added by intruder.
That there is activity on that particular port. There may be services accessing the particular port. Moved files, and new accounts. Created new directories.
Yes, he has basically complete administrative access to the computer.
The intruder has created a new administrator account. The intruder has installed a back door. The intruder has also created a shared drive. Finally, the intruder puts the file cmd.exe onto the system and leaves it (he changed what the program did).
7. The MD5 checksums will be different.
8. We use HashCalc to compare hashes between the checksums.
9. The recommendation would be to patch the original vulnerability to put the system back in production. Doing things such as getting rid of the backdoor, removing the share, and deleting the administrator account that was created by the intruder.
10. The file that was dropped in the computer was cmd.exe.
Screenshot 1 -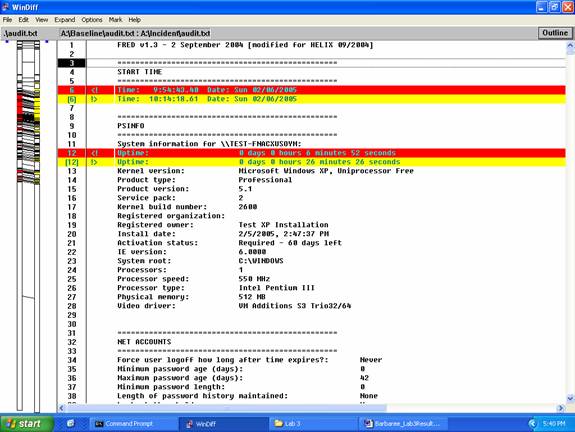
Screenshot 2 - 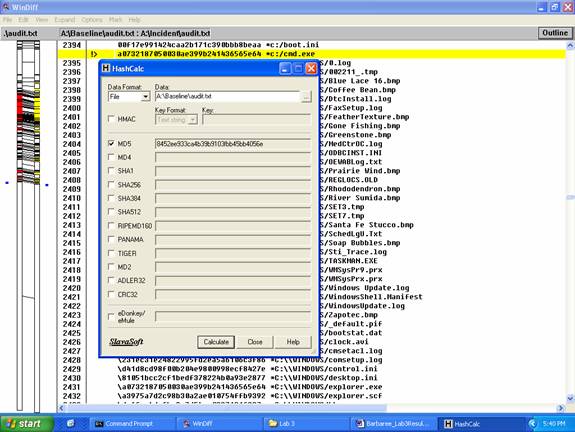
Screenshot 3 - 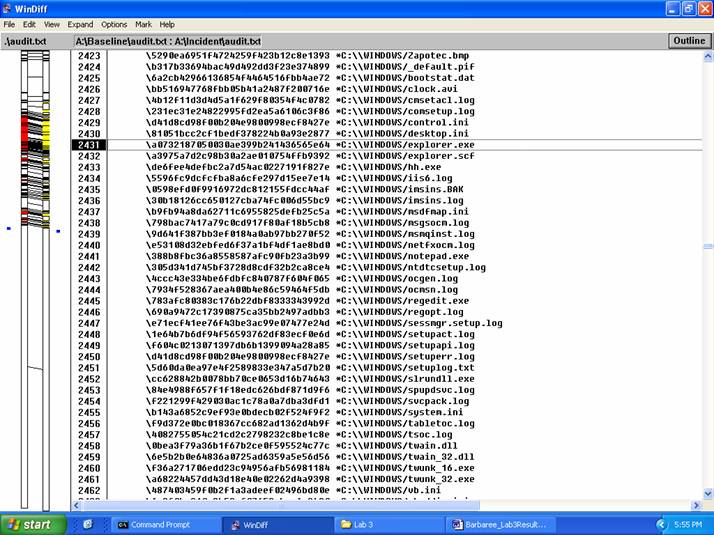
|