![]()

Operating System
Security Configuration Tool Set
White Paper
Abstract
This paper describes the Microsoft Security Configuration Tool Set, a set of Microsoft Management Console (MMC) snap-ins designed to reduce costs associated with security configuration and analysis of Windows NT® and Windows® 2000-based operating system networks. The Security Configuration Tool Set allows you to configure security for a Windows NT or Windows 2000-based system, and then perform periodic analysis of the system to ensure that the configuration remains intact or to make necessary changes over time. It is also integrated with Windows Administration Change and Configuration Management to automatically configure policy on a large number of systems in the enterprise.
© 1999 Microsoft Corporation. All rights reserved.
The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication.
This white paper is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT.
Microsoft, Active Desktop, BackOffice, the BackOffice logo, MSN, Windows, and Windows NT are either registered trademarks or trademarks of Microsoft Corporation in the United States an 23223p1514x d/or other countries.
Other product and company names mentioned herein may be the trademarks of their respective owners.
Microsoft Corporation .
|
Contents |
Introduction
Why the Security Configuration Tool Set Is Necessary
Security Configuration Tool Set Design Goals
Security Configuration Tool Set Features
Comprehensiveness
Flexibility
Extendibility
Simplicity
Security Configuration Tool Set Overview
Security Configuration Tool Set Components
Security Configurations
Security Configuration and Analysis Database
Security Configuration and Analysis Areas
Security Configuration Tool Set User Interfaces
Graphical User Interfaces
Secedit Command
Configuring Security
Account Policies
Local Policies and Event Log
Restricted Groups
Registry Security
File System Security
System Services Security
Analyzing Security
Account and Local Policies
Restricted Group Management
Registry Security
File System Security
System Services Security
Group POLICY INTEGRATION
Security Configuration in Group Policy Objects
Additional Security Policies
Using the ToolS
Using Security Configuration Editor
Using Security Configuration Manager
Using Security Settings Extension to Group Policy Editor
For More Information
Appendix A. Implementing Security Attachments
Introduction
Architecture
Building the Attachment Engine DLL
The Data Structures
Security Configuration Tool Set Callback and Helper APIs
Parameters
Return Values
Return Values
Parameters
Return Values
Parameters
Parameters
Return Values
Parameters
Return Values
Required Attachment Interfaces
Syntax
Parameters
Return Values
Syntax
Parameters
Return Values
Syntax
Parameters
Return Values
Installation and Registration
Building the Extension Snap-in
Clipboard Format
Extension Snap-in Interfaces
Installation and Registration
Initialization-Adding the Attachment Node
Implementing ISceSvcAttachmentPersistInfo
Introduction |
This paper describes the Microsoft Security Configuration Tool Set, a set of Microsoft Management Console (MMC) tools designed to simplify, integrate, and centralize security configuration and analysis tasks for Windows NT® and Windows® 2000-based systems. The Microsoft Management Console is a Windows operating system-based multiple-document interface (MDI) application that makes extensive use of Internet technologies. MMC is a core part of the Microsoft management strategy and is designed to provide a single host for all management tools, facilitate task delegation, and lower total cost of ownership for enterprise users of Windows and Windows NT. MMC itself does not supply any management behavior, but instead provides a common environment for snap-ins, which define the actual management behavior. Snap-ins are administrative components integrated into a common host-the MMC interface.
The Security Configuration Tool Set is a set of snap-ins for MMC that is designed to provide a central repository for security-related administrative tasks. With Security Configuration Tool Set, you will be able to use an integrated set of tools to configure and analyze security on one or more Windows 2000 or Windows NT-based machines in your network.
The current version of the Microsoft Windows NT operating system has excellent security features built in. A single logon to the Windows NT-based domain allows user access to resources anywhere in the corporate network. The system provides tools for security policy and account management, and the Windows NT domain model is flexible and can support a wide range of network configurations. Windows 2000 extends these features to provide support for Internet-aware enterprise networks and the new distributed services included in the operating system.
From the administrator's point of view, Windows NT provides a number of graphical tools that can be used individually to configure various aspects of system security. However, these tools are not centralized-an administrator may need to open three or four applications to configure security for one computer. Using these applications can therefore be costly and cumbersome for many security-conscious customers. In addition, security configuration can be complex-and with the distributed security features added in Windows 2000, this complexity has increased.
While Windows NT 4.0 does provide adequate (if somewhat inconvenient) configuration tools, it lacks tools for security analysis. The only tool in this category is Event Viewer, which was not designed for performing corporate-level audit analysis. There are some third-party tools for such purposes; however, even most of those tools either lack enterprise-level features or are not comprehensive.
The Security Configuration Tool Set is intended to answer the need for a central security configuration tool and will provide the framework for enterprise-level analysis functionality in future versions. Most importantly, it will reduce security-related administration costs by defining a single point where the entire system's security can be viewed, analyzed, and adjusted, as necessary. The goal is to provide a comprehensive, flexible, extensible and simple tool set for configuring and analyzing system security.
The primary goal of the Security Configuration Tool Set is to provide a single point of administration for Windows NT and Windows 2000-based system security. To meet that goal, the tool must allow the administrator to:
Configure security on one or more Windows NT or Windows 2000-based computers.
Perform security analysis on one or more Windows NT or Windows 2000-based computers.
Complete these tasks from an integrated and uniform framework.
The process of configuring security in a Windows NT or Windows 2000-based network can be complex and detailed in terms of the system components involved and the level of change that may be required. Therefore, the Security Configuration Tool Set is designed to allow you to perform configuration at a macro level. In other words, the tool set allows you to define a number of configuration settings and have them implemented in the background. With this tool, configuration tasks can be grouped and automated; they no longer require numerous, iterative key presses and repeat visits to a number of different applications to configure a group of computers.
The Security Configuration Tool Set is not designed to replace system tools that address different aspects of system security-such as User Manager, Server Manager, Access Control List (ACL) Editor, and so on. Rather, its goal is to complement them by defining an engine that can interpret a standard configuration file and perform the required operations automatically in the background. Administrators can continue to use existing tools (or their newer versions) to change individual security settings whenever necessary.
To address the security analysis gap in Windows NT security administration, the Security Configuration Tool Set provides analysis at a micro level. The tool set is designed to provide information about all system aspects related to security. Security administrators can view the information and perform security risk management for their entire information technology (IT) infrastructure. In future versions, they will be able to create reports and perform specialized queries.
The Security Configuration Tool Set is designed to be comprehensive, flexible, extendible, and simple.
Unlike other operating system features, security is a characteristic of the system as a whole. Almost every component of the system is responsible for some aspect of system security. Therefore, questions such as "Is my computer secure?" or "Is my network secure?" become extremely difficult to answer. Typically, a system administrator must examine many different system components and use many tools in an attempt to answer these questions. The goal is for the Security Configuration Tool Set to be the resource for answering security-related questions, whether they are general (such as those listed above) or very specific. To provide comprehensive security administration and information, the Security Configuration Tool Set allows you to configure and analyze all of the following:
Account policies-You can use the tool to set access policy, including domain or local password policies, domain or local account lockout policy, and domain Kerberos policy.
Local policies-You can configure local audit policy, user rights assignment, and various security options such as control of floppy disk, CD-ROM, and so forth.
Restricted groups-You can assign group memberships for built-in groups such as administrators, server operators, backup operators, power users, and so on, as well as any other specific group that you would like to configure. This should not be used as a general membership management tool-only to control membership of specific groups that have sensitive capabilities assigned to them.
System services-You can configure security for the different services installed on a system, including network transport services, such as TCP/IP, NetBIOS, CIFS file sharing, printing, and so on. These can be configured as start-up options (automatic, manual, or disabled), or you can also set access control on these services-grant or deny access to start, stop, pause, and issue control commands.
File or folder sharing-You can configure settings for Windows NT File System (NTFS) and Redirector service. These include options to turn off anonymous access and to enable packet signatures and security when accessing various network file shares. Future releases will include other service-specific sub-areas, including services such as the Internet Information Server.
System registry-You can use the tool set to set the security on system registry keys.
System store-You can use the tool set to set the security for local system file volumes and directory trees.
Directory Security - You can use the tool set to manage the security on objects residing in the Windows 2000 Active DirectoryT.
The Security Configuration Tool Set allows you to define security configurations that include settings for security attributes in each of the areas outlined above. Using these configurations, you can configure the system.You can also perform security analysis on the system by using these configurations as recommendations.
The configurations are saved in text-based .inf files. Configuration information is specified in different sections, and the information is parsed by the tool set's configuration engine. The architecture is sufficiently flexible to support new sections if you need to specify new areas of security configuration and analysis as the system evolves.
The Security Configuration Tool Set includes a set of predefined configurations that will ship with the first release. You can choose to use these configurations as shipped, or you can use them as starting points for building your own customized configurations. The tool set's configuration editing tool, called the Security Configuration Editor, provides this capability.
The Security Configuration Tool Set is designed to be extendable. You can add extensions as new areas of security configuration and analysis, or as new attributes within an existing area. Since the configuration information is stored in a standard .inf file format, it can easily be extended without affecting backward compatibility.
Additionally, system services is a currently defined area that has been designed to be extendable. It permits any service writer to implement a security configuration attachment that can configure security settings for their particular service, as well as perform any analysis that may be required. Different Windows NT-based systems can be configured to run different sets of services. Also, Microsoft expects that independent software vendors (ISVs) who develop services will want to add their service's security configuration and analysis to this overall security framework. The tool set initially supports the security configuration attachment for the native Windows NT service for network file sharing (CIFS). Future releases will include attachments for IIS, and so on.
Because the Security Configuration Tool Set is designed to reduce costs associated with administering security on a network, it is vital that the tool be easy to learn and use. The tool set contains no complicated options-only a simple uniform graphical user interface (GUI) for defining configurations, saving them to files, and viewing security analysis data stored in the security analysis database. The interface uses the standardized context menus and views supported by Microsoft Management Console. There are no superfluous graphics or statistics, only a simple tabular view of the information with visual cues to flag security problems. In addition, the tool set contains a command-line utility, Secedit.exe, to allow administrators to run configuration and analysis as part of a script. Administrators can use the graphical interface or the command line to apply a saved configuration and perform analysis, enabling them to easily fit the tool into an existing administration model.They can also use the graphical interface to define configurations and browse through analysis data.
The next section of this document provides a more in-depth overview of the Security Configuration Tool Set, its architecture and how it fits into Windows NT and Windows 2000.
Security
Configuration
|
The Windows NT and Windows 2000 Distributed Security Services include many new features to simplify domain administration, improve performance, and integrate Internet security technology based on public-key cryptography. Highlights of the Distributed Security Services include:
Integration with the Windows 2000 Server Directory Service (the Active Directory) to provide scalable, flexible account management for large domains, with fine-grain access control and delegation of administration.
Kerberos version 5 authentication protocol, a mature Internet security standard, is implemented as the default protocol for network authentication and provides a foundation for authentication interoperability.
Strong authentication using public-key certificates, secure channels based on Secure Sockets Layer version 3.0, and CryptoAPI version 2.0 deliver industry-standard protocols for data integrity and privacy across public networks.
The security enhancements were specifically designed to meet the needs of distributed enterprise networks. While security services in Windows 2000 are impressive, the need for a tool to configure and administer such capabilities easily is obvious. The Security Configuration Tool Set, a Microsoft Management Console snap-in, fills this need. (For a detailed description of the Microsoft Management Console, see the white paper entitled "Microsoft Management Console: Overview" at microsoft.com.)
The tool set consists of following components:
Security Configuration Service-This service is the core engine of the Security Configuration Tool Set. It runs on every Windows 2000-based system and is responsible for all security configuration and analysis functionality provided by the tool set. This service is central to the entire infrastructure.
Setup Security-The initial security configuration done during setup is performed by this tool set, using predefined configurations that ship with the system. This creates an initial security database, called the Local Computer Policy database, on every computer with a clean installation of Windows 2000.
Note This is not the case when a Windows NT 4.0 or earlier-based machine is upgraded because a customer may have customized the security configuration, which must not be overwritten. In this case, the customer can use the Configure option of the tool set to apply a configuration.
Security Configuration Editor-This stand-alone snap-in tool allows you to define computer-independent security configurations, which are saved as text based .inf files.
Security Configuration Manager-This stand-alone snap-in tool allows you to import one or more saved configurations to a security database (it may be the local computer policy database or any private database). Importing configurations builds a machine-specific security database, which stores a composite configuration. You can apply the composite configuration to the computer and analyze current system configuration against the stored composite configuration stored in the database.
Security settings extension to the Group Policy Editor-This snap-in tool extends the Group Policy Editor. It allows you to define security configuration as part of a group policy object. Group policies are part of the Microsoft Windows Administration initiative. For more information on Group Policy and Windows Administration, see https://www.microsoft.com
Group policy objects can then be assigned to a specific computer, or at the domain or organizational unit scope in Active Directory, so that they are applied to all computers in that scope. Security configurations from various group policy objects (local, domain, and organizational units) are propagated to the computer and imported into the local computer policy database on that computer. The composite configuration from this database is applied to the computer periodically to ensure that the system adheres to corporate policy. This is referred to as the computer's security policy.
Command-line tool: Secedit.exe-This is the command-line interface to some of the features of the tool set.
The Security Configuration Editor allows you to define security configuration files with prescribed security settings for attributes in each security area (areas include account policies, local policies, restricted groups, the registry, and so on). Security configuration files are standard text-based .inf files. Using the Security Configuration Manager, you can import these saved configurations to the security database on different computers. You can also import these configurations into Group Policy objects and have them propagate automatically to the local computer policy database.
The Security Configuration Editor snap-in provides a graphical user interface that allows you to edit security configuration files to define customized configurations. It provides cut-and-paste capabilities, allowing you to copy parts of configurations from different files and create a new customized configuration. (See Figure 1.)

Figure 1. The Security Configuration Editor
As shipped, the Security Configuration Tool Set includes standard and recommended configurations that are effective in typical Windows NT and Windows 2000 configurations, including those installations that have Internet and intranet components. The predefined configurations include various recommendations made in the white paper "Securing Windows NT Installations" at microsoft.com). In addition, the editing capabilities of the snap-in allow you to use the predefined security configuration files or create new ones by customizing them for your particular environment.
The security configuration and analysis database (security database) is a computer-specific data store that is generated when one or more configurations are imported to a particular computer. There may be an initial database created when a computer has a clean installation of Windows 2000. This database is referred to as the local computer policy database. Initially, it contains the default out-of-the-box security configuration of your system. You may export this configuration to a security configuration file, immediately after the installation and save it. This is useful if you want to restore initial security configuration at any later point, for any reason.
A security configuration and analysis database is the starting point for all configurations and analyses done on a system. The database is initially created from a computer-independent configuration file described above. New configurations can be incrementally added to the database without having to overwrite the entire configuration. (See Figure 2.)

Figure 2. Menu on the Security Configuration Manager showing how databases can be selected and/or created
The local computer policy database is the special security database on the system. It defines the security policy in force for that system. At any time, the system runs with the configuration defined in the policy. Policy may not define the entire configuration. This means that various configuration attributes can be ignored. For example, security for every file or folder path may not be defined. This implies that security configuration attributes that are not enforced by policy may take any value-default or defined by some other mechanism, such as the ACL Editor in Windows Explorer for files and folder security. Things that are not enforced by policy may also be configured manually using personal databases. However, any custom configurations that conflict with the policy are overridden by the definitions in the policy. Personal database configurations are useful in areas like the registry and the file system, where multiple users on the system can secure their own registry hive and home directory subtrees.
Another important aspect of the security database is its use in performing analysis. You can use the Security Configuration Manager to perform a comparison of the current system configuration against the stored configuration in the database. Performing the analysis provides you with information on where a particular system may be deviating from a particular configuration. This helps you in troubleshooting problems, tuning the security policy, and most importantly, detecting any security flaws that may open up in the system over time. (See Figure 3.)

Figure 3. The Security Configuration Manager showing analysis
Security configuration for a system is subdivided into security areas, as stated previously. Microsoft has identified several security areas; however, new areas can be added in the future to support enhanced system functionality without breaking backward compatibility with existing configuration files and databases. The currently supported security areas are:
Account policies-This area allows you set passwords, account lockout, and Kerberos policies. Kerberos policies are relevant only on Windows 2000 domain controllers.
Local policies-This area allows you to configure audit policy, user rights assignment, and computer security options.
Restricted groups-These settings manage group memberships for selected groups that you may consider sensitive.
Object trees-There are three security areas in this category:
For each object tree, defined configuration files allow you to configure (and analyze) settings for security descriptors, including object ownership, the Access Control List (ACL), and auditing information.
System services-This area includes all local or network system services. This security area is designed so that independent software vendors (ISVs) can build Security Configuration Tool Set attachments for configuration and analysis of specific system services. In addition, Microsoft will build attachments for some services that are shipped with the system. The first release will include an attachment for configuring and analyzing security on the Network File Sharing service. See Appendix A, Implementing Service Security Attachments, for implementation and installation instructions on this topic.
The Security Configuration Tool Set GUI is provided as a set of Microsoft Management Console (MMC) snap-ins. The graphical interface supports the following administrative functions:
Defining security configurations-The tool set includes the Security Configuration Editor, which allows you to define and save a configuration. Since configurations are saved as text-based .inf files, you can use any text editor to read the sample configuration provided with the tool and learn their format; however, Microsoft does not recommend using your text editor to alter a configuration file. In doing so, you could inadvertently alter the format of the file so that it cannot be parsed by the Security Configuration Service engine. Instead, use the Security Configuration Editor snap-in to create or change a configuration file.
To use the Security Configuration Editor, start MMC and add the Security Configuration Editor stand-alone snap-in and all its extensions into a new MMC console, which may be saved for future use. For more information, read the help documentation on Microsoft Management Console.
Configuring system security To configure a Windows NT or Windows 2000-based system's security, you can use one of the options in the tool set:
Security settings extension to the Group Policy Editor-This option is recommended for configuration if you have an Active Directory-based Windows infrastructure. It can also be used locally on individual computers with or without the Active Directory. In the local case, a group policy object is configured locally on a computer. To use this option, start the Group Policy Editor and point to an appropriate group policy object, which may be the one stored in the Active Directory or the one locally on a computer. Click Computer Settings, and then click Security Settings The node name space that you see here is identical to what is present in the Security Configuration Editor, where you edit a particular configuration. You can copy-and -paste specific nodes (each representing a particular security area) from SCE into the corresponding node in Group Policy or you may import an entire configuration into Group Policy. This causes the security configuration to be saved in a group policy object and to be applied as part of group policy enforcement. Group policy objects are applied to a computer, based on the Active Directory scope (domain and organizational units) that the computer is under. This can cause several security configurations to be applied to the computer. If they contain the same attributes, the last writer wins, based on the order of applying group-policy objects. For more information on the group policy infrastructure, see "Windows 2000 Group Policy" at microsoft.com.
Security Configuration Manager-This option is recommended for configuration only when you do not have an Active Directory-based Windows infrastructure and you do not need to have the security configuration applied periodically; in other words, you would rather control configuration and analysis manually. To use this, start MMC and add the Security Configuration Manager snap-in and its extension snap-ins. By default, the snap-in points to the local computer policy database. You may choose to switch to a different database by right-clicking on the Security Configuration Manager node, and then clicking Set Database from the Context menu. On the SCM, select Import Configuration from the Context menu. This opens the File Open dialog box, which you use to browse to a saved configuration and select it. Repeat this process by importing additional saved configurations as incremental settings. The database merges various configurations to create one composite configuration, resolving conflicts with the last-writer-wins rule. Once the configurations are imported to the selected database, click Configure Now from the Context menu to apply it to the system. A progress dialog box shows you how the configuration is being applied and will finally show you the error log, if errors are encountered in the process.
Secedit command-line tool-This option is recommended when you do not have an Active Directory-based infrastructure and have several computers that need to be configured frequently. Start a console window, and specify Secedit.exe; then select the applicable options, such as, where the security database should be kept, which configuration(s) to use, and so on. You can also create command batch files, and then schedule them to run at off-hours, using the task scheduler. You can use Microsoft System Management Server to distribute this task on several different computers.
Note The tool set supports the capability to apply multiple configurations. You can choose to apply a small configuration initially and then add configurations to it. The security database stores the merged form of the multiple configurations, and the latest configuration settings override any previous value for the same setting.
Analyzing system security To analyze system security, either click Analyze on the Context menu within the Security Configuration Manager snap-in, or use the command-line utility to collect the analysis to a security database. This can be done in the form of an administrative script that can be run immediately or when most convenient using. You can also use the System Management Server to distribute this task on various different computers.
View security analysis data-The Security Configuration Manager allows you to see the security information in each security area. Saved configuration recommendations are presented alongside current collected system settings, and icons are used to highlight any problem areas where the current settings do not match the ones saved in configuration. You can correct the problems by reconfiguring the system by clicking Configure Now. from the Context menu. The SCM also allows you modify the saved configuration settings to match the current system setting. You can then preserve the current setting, which is reflected in the database. Future analyses will no longer show the problem. This can also be used to make any on-the-fly changes that need to be applied.
Note While various graphical user interfaces provide all of the functionality listed above, the command-line utility supports configuring the system and collecting analysis data only. It does not support the creation or editing of configurations or the viewing of analysis data.
The following graphical user interfaces are provided with the tool set:
Security Configuration Editor-This is a stand-alone snap-in that allows editing capabilities for security configurations. (See Figure 4.)

Figure 4.The Security Configuration Editor
Security Configuration Manager-This is a stand-alone snap-in that allows importing configurations to a security database, configuring the system with any saved (composite) configurations in the database and analyzing the current security state against the saved configuration and reporting any discrepancies. (See Figure 5.)

Figure 5.The Security Configuration Manager
Security Settings Extension-This is an extension snap-in to the Group Policy Editor. It allows saving a security configuration as part of group policy objects, which can then be assigned to individual computers or groups of computers and automatically applied. (See Figure 6.)

Figure 6. Security settings extension to the Group Policy Editor, showing the GPE scoped at the local computer policy
Figure 7 shows the usage parameters available with the Security Configuration command-line utility, Secedit.

Figure 7. Secedit command-line utility
The command syntax is:
secedit
Syntax details for each Secedit option are described below.
The following analyzes system security:
secedit /analyze [/scppath scppath] [/sadpath sadpath] [/log logpath] [/verbose] [/quiet]
where
/sadpath sadpath is the path to the database that Secedit performs the analysis against. Analysis results are stored in this database, along with the configuration information already there. If sadpath is not specified, then a default database, is used. The default database is %windir%\security\database\ secedit.sdb for admins or userprofile%\secedit.sdb for Users. If sadpath is a new database, the scppath must be specified.
/scppath scppath is the path to a configuration file that should be loaded into the new database prior to performing the analysis. If scppath is not specified, the analysis is performed against the configuration information already contained in the sadpath database. Scppath is only valid when sadpath is a new database.
/log logpath is the path to log file for the process. If not provided, the default %windir%\security\logs\scesrv.log is used.
/verbose instructs Secedit to provide detailed progress information.
/quiet instructs Secedit to suppress screen and log output.
The following configures security for the system:
secedit /configure [/scppath scppath] [/areas areas] [/overwrite][/sadpath sadpath] [/log logpath] [/verbose] [/quiet]
where:
/sadpath sadpath is the path to database that Secedit will use to configure the system (with addition of information in scppath if a scppath is specified.) If sadpath is not specified, then a default database is used. The default database is %windir%\security\database\secedit.sdb for administrators or %userprofile%\secedit.sdb for users. If sadpath is a new database, the scppath must be specified.
/scppath scppath is the path to a configuration file that should be loaded into the database prior to performing the configuration. If scppath is not specified, the system is configured using the configuration information already contained in the sadpath database.
/areas areas specifies the security areas to be processed, as follows:
The default is all areas. Each area should be separated by a space.
/log logpath is the path to the log file for the process. If not provided, the default %windir%\security\logs\scesrv.log is used.
/verbose instructs Secedit to provide detailed progress information.
/quiet instructs Secedit to suppress screen and log output.
/overwrite specifies that configuration information loaded from scppath should overwrite any existing configuration information currently maintained in the database. Any future configurations using this database are based solely on the information specified in the scppath file. If Overwrite is not specified, information from the scppath file is appended to any existing information in the sadpath database. Overwrite is valid only if scppath is specified.
The following generates a configuration file from the database:
secedit /generate /scppath scppath [/areas areas][/sadpath sadpath] [/log logpath] [/verbose] [/quiet]
where:
/sadpath sadpath is the path to database that Secedit will use to obtain system configure information. If sadpath is not specified, then a default database is used. The default database is %windir%\security\database\secedit.sdb for administrators or %userprofile%\secedit.sdb for users. If sadpath is a new database, the scppath must be specified.
/scppath scppath is the path to a file where the configuration information will be saved. Scppath must be specified for this operation.
/areas areas specifies the security areas to be processed, as follows:
The default is all areas. Each area should be separated by a space.
/log logpath is the path to the log file for the process. If not provided, the default %windir%\security\logs\scesrv.log is used.
/verbose instructs Secedit to provide detailed progress information.
/quiet instructs Secedit to suppress screen and log output.
The following starts security policy propagation in the background:
secedit /RefreshPolicy
where
RefreshPolicy instructs Secedit to refresh the security policy as follows:
The following validates the syntax of a Security Configuration Editor configuration file:
secedit /validate filename
where
validate filename specifies the configuration file to validate.
Configuring Security |
This section describes how to use the Security Configuration Tool Set to configure various security aspects of a Windows 2000-based system. These tools rely entirely on the security features of Windows 2000- they do not alter the security capabilities of the system. The sole purpose of the tool set is to allow you to more easily configure and manage the advanced security features included in the latest version of the operating system.
In Windows 2000, there are two kinds of accounts-domain accounts and local accounts. Account policies for domain accounts are configured at the domain, and account policies for local accounts are configured locally at the computer. This allows very fine-grained security control, but can be difficult to configure. Figure 8 shows the configuration view for account policies.

Figure 8. Configuring account policies
A domain's account policy defines how strong the passwords have to be, the password history, the lifetime of Kerberos tickets, account lockouts, and so on. You can define all of these attributes from the security configuration. Similarly, locally on a computer, you can specify the same policies for local accounts. The only exception to this is Kerberos policy, which does not exist for local accounts, which are not authenticated using Kerberos.
In Windows 2000, local policies by definition are local to a computer with no distinction between different computers (domain controllers, servers, or workstations). Local policies include auditing policy, user rights and privilege assignment, and various security options that may be configured locally on a particular Windows 2000-based computer.
Auditing policy allows you to configure what security events are set in the security log on that computer.
User rights and privilege assignment allows you to control who is granted rights and privileges on a given system.
Security options allow you to control who has access to items, such as the floppy drive and CD-ROM.
As with account policies, local policy may be configured or analyzed using multiple options available from the tool set. Figure 9 shows some of the options available for configuring local policies.

Figure 9. Configuring local policies
The restricted group area allows you to manage the members of built-in groups that have certain predefined capabilities. These groups include built-in groups such as administrators, power users, print operators, server operators, and so on, as well as domain groups, such as domain administrators.
You can also add groups that you consider sensitive or privileged to the Restricted Groups list, along with their membership information. This allows you to track and manage these groups as part of system security configuration or policy.
In addition to group members, the area tracks and controls reverse membership of each restricted group in the Members Of column. This column shows other groups to which the restricted group can belong. You can use this field to control exactly which groups your restricted group members can join-you can also use this feature to limit a group of users to one group and prevent them from joining any others. (See Figure 10.)

Figure 10. Configuring restricted groups
Applying the configuration ensures that group memberships are set as specified in the configuration file. Groups and users that are not specified are removed from the restricted group. In addition, the Reverse Membership Configuration option ensures that each restricted group is a member of only those groups specified in the Member Of column.
The registry is another object tree in which the Security Configuration Tool Set allows you to manage the object by placing a security descriptor on the object. In the case of the registry, however, the objects are registry keys. Again, the configuration contains the full registry key path and security descriptor in SDDL format.
Because Windows 2000 supports a dynamic inheritance model for all object providers, when applying security on registry keys, the Security Configuration Tool Set follows the same inheritance algorithm as the directory tree. The snap-in's configuration layout for registry security configuration is shown in Figure 11.

Figure 11. Configuring registry security settings
Local file system security is the third object tree supported within the Security Configuration Tool Set. It treats all volumes on a system as part of a single tree, with first-level nodes as the root directory of each volume. This is similar to the directory and registry security configuration in that the configuration file contains a list of fully qualified file or directory paths and security descriptors for each. The dynamic inheritance model is supported on NTFS files, also. The snap-in's configuration layout for file system security is illustrated in Figure 12.

Figure 12. Configuring file system security settings
System Services include critical functionality, such as network services, file and print services, telephony and fax services, and Internet/intranet services. Because of the breadth and diversity of this area, the Security Configuration Tool Set's system services area is designed to be extendable. The Security Configuration Tool Set directly supports general settings for each system service. These general settings include the service startup mode (automatic, manual, or disabled) and security on the service. The name of the service must be the same as the one used by the Service Control Manager. (See Figure 13.)

Figure 13. Configuring system services security
To extend this area of the Security Configuration Tool Set so that it can be used to configure specific settings for a new service, create and attach a security configuration attachment, which consists of the following:
An engine DLL that exports three well-defined interfaces. Implementing all of these interfaces is optional. One interface is used to configure settings, another query settings for analysis (discussed below), and the third update settings. You can choose to implement only configuration, only analysis, or both. You can choose to support user editing of stored configuration in the database. You must register the name of this DLL in a well-known place in the registry, along with the name of the service to which it applies. The Security Configuration Engine service looks up the registry key to get the list of services, and loads each attachment DLL. The Security Configuration Engine then calls the appropriate interface, depending on whether it is configuring a system or collecting analysis information. The interface communicates with the attachment, which is then responsible for saving the configuration or analysis information in the specified section within the configuration and using that information to configure the system or to alert the administrator.
An extension snap-in, which extends the Security Configuration snap-ins (the Editor and the Manager) within the Microsoft Management Console. The extension snap-in consists of a scope pane node-with its own name space-that extends the services node to support service-specific settings. The extension snap-in also needs to export well-defined interfaces to communicate with the Security Configuration snap-ins. The extension snap-in does not communicate directly with its engine DLL. An extension snap-in provides functionality only when invoked by a parent snap-in (in this case the Security Configuration Tool Set).
An installation kit that registers the engine for the Security Configuration Tool Set and the extension snap-in.
Figure 14 shows the pieces of the attachment and how they fit into the Security Configuration Tool Set snap-in and MMC.
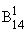
Figure 14. Security Configuration Tool Set and attachment architecture
Microsoft provides attachments for some services that are shipped with the system. In its initial release, Microsoft plans to ship a security configuration attachment for the CIFS File Sharing Service.
In addition, the interface used to extend the tool set is described in Appendix A, Implementing Service Security Attachments.
Analyzing Security |
This section describes how to use the Security Configuration Tool Set to analyze various security aspects of a Windows 2000-based system. The Security Configuration Tool Set provides a graphical interface that allows you to view the analysis information collected from the system.You can also use the Security Configuration Manager or the command-line utility, secedit, to collect analysis data from the system. This enables you to collect the data interactively or to schedule data collection as part of an off-hour batch processing script, using the System Management Server or the task scheduler.
To promote ease of use (and to eliminate the steep learning curve normally associated with new administration tools), the GUI design of the analysis display has been kept simple and informational. Instead of complicated graphics or error alerts, it provides simple visual cues (icons) to identify security problems, and provides the information required to fix those problems. The interface uses a simple table that lists the attributes, their corresponding values, and the recommended values. Potential problems are identified by changes in icon.
The Security Configuration Tool Set uses the composite configuration present in the database when performing its security analysis. The composite configuration lists the preferred or recommended settings and is necessary to do comparisons and to provide recommended configuration information so that potential problems in the current system settings can be found and fixed. The Security Configuration Tool Set engine queries settings for various security attributes in each of the security areas and compares the values to the recommendations in the composite configuration. If the system settings match the configuration, they are assumed to be correct. If not, they are identified as potential problems that need investigation. These potential problems are noted and displayed in the Security Configuration Manager interface.
By default, the composite configuration is the one used during system configuration. You can update the composite configuration by making edits, importing additional configurations, or completely replacing it with a new configuration. The analysis information is collected by the engine and stored in the standard Microsoft ISAM database technology. The use of standard Microsoft database technology is intentional. It will provide for integrated reporting mechanisms and high-end capabilities, such as querying, transactions, and so on. ODBC support will also be provided.
In addition to analyzing the system's current configuration, the Security Configuration Manager interface allows you to make interactive changes of two kinds: you can change the system configuration, or you can change the stored configuration.
Changing the system configuration involves updating the system settings so that they match the ones recommended by the composite configuration stored in the database. Choosing the Configure option reapplies all of the settings specified in the composite configuration stored in the database.
Changing the composite security configuration involves updating the configuration stored in the database to reflect a new system setting. You can use this option to tell the tool set not to inform you of specific non-standard settings that you have investigated and consider reasonable. You can also make changes to stored configurations by importing additional configuration files or replacing the currently assigned configuration with a new one.
The Security Configuration Manager provided with the Security Configuration Tool Set displays the system security configuration information organized into security areas, as defined previously in this document. The next sections describe the analysis capabilities associated with each area.
When analyzing system security, the Security Configuration Tool Set queries all of the defined security attributes that fall in this area and saves them in the current analysis section of the database. You can then use the Configuration Manager to see the information.
The Security Configuration Manager provides a tabular view of the information. For each attribute, it displays the current and recommended settings (recommended settings are obtained from the composite configuration in database). Attributes that are not the same as the recommended settings are clearly identified by different icons so that you can easily recognize and correct problems. To correct a problem, you can either accept the current setting, in which case the value in the stored configuration is modified, or you can change the system setting to match the recommendation, in which case the corresponding attribute is reset when the system is reconfigured.
Figure 15 shows the Configuration Manager displaying security policies information.

Figure 15. Analyzing account and local policy settings
Analysis of restricted groups involves tracking group memberships, including recursive membership. Problems are identified using different icons. To correct a problem, you can either accept the current settings, in which case the stored configuration is modified, or you can change the system setting to match the recommendation, in which case the problematic group memberships are changed when the system is reconfigured.
Figure 16 shows the Configuration Manager displaying restricted group management information.

Figure 16. Analyzing restricted group membership
The Security Configuration Tool Set's engine uses the
paths to the registry keys and their security descriptors (the paths and
descriptors are stored in SDDL format in the composite configuration) as the
basis for its analysis. The engine analyzes the registry information and
provides information about the similarity of security descriptors to the ones
defined. The engine again uses OK, Investigate, and Not Configured to
categorize the security descriptor information on the actual tree, as compared
to that in the stored configuration.
Figure 17 shows the Configuration Manager displaying registry security
information.

Figure 17. Analyzing registry security settings
Local file system security is the third object tree supported within the Security Configuration Tool Set. The Security Configuration Tool Set analysis engine uses the list of fully qualified file or directory paths and their security descriptors stored in the assigned configuration as the basis for its analysis. The engine analyzes the information and determines the similarity of the actual security descriptors to the ones defined. The analysis engine again uses OK, Investigate, and Not Configured to categorize the security descriptor information on the actual tree, compared to that in the configuration.
Figure 18 shows the Configuration Viewer displaying local file system security information.

Figure 18. Analyzing file system security settings
Security Configuration Tool Set collects general security information on all services configured to run on the system. General information includes startup settings and security descriptors. The tool set detects problems, such as mismatches or services not specified in the configuration, and reports them.
Analysis of service-specific security settings for each service is also provided by the service security attachment architecture for the Security Configuration Tool Set, as discussed in the configuration section above. In this case, the Security Configuration Tool Set calls the defined interfaces to allow the attachment to collect the necessary data and store it in a specific place in the database. The Configuration Manager then calls the extension snap-in's analysis interface to display the information, as well as to accept user actions to correct problems. (See Figure 19.)

Figure 19. Analyzing system services settings
As stated previously, Microsoft will ship a security configuration attachment for the CIFS File Sharing Service in the initial release of the Security Configuration Tool Set. The file sharing attachment allows you to configure and analyze following security information about the service:
Policies-Enabling or disabling packet signatures on network packets for both server and client side, anonymous access to shares and pipes, and so on.
Shares-Security on various shares that are made available from the computer.

Figure 20. Analyzing file sharing settings
The interface used to extend the tool set is documented in Appendix A, Implementing Security Attachments. This interface allows ISVs to build security attachments for other services.
Group POLICY INTEGRATION |
As discussed above, another important piece of the Security Configuration Tool Set is its integration with the Group Policy infrastructure developed for the Microsoft Windows Administration initiative. The goal of this initiative is to allow administrators to configure a large number of clients by setting policies on the server side and have them automatically propagated and applied to the clients. Group Policy uses the Active Directory to allow computers and users to be grouped based on scope. The scope is defined at one of the following levels: sites, domain, or organizational units. Advanced support allows subset grouping within an organizational unit. Limited group policy may also be defined locally on individual computers where it is referred to as local computer policy. For more information about this infrastructure, see the white papers on Windows Administration and Group Policy at https://www.microsoft.com.
One of the policies that can be configured and propagated is security policy. Security policy is defined as a security configuration file that is stored as part of a group policy object. This security configuration file is identical to the one used everywhere else in the tool set. Therefore, the areas covered by the security part of the group policy include:
Account policies
Local policies
Restricted groups
System services
Registry
File system
Directory objects
Figure 21 shows the layout of the security portion of the group policy object. Click Computer Settings, and then Security Settings to get to the security portion of the group policy object, which looks identical to the configuration layout in the Security Configuration Editor and the Security Configuration Manager. There is integrated support between the tools to allow cut and paste between the same nodes, as well as the ability to export configuration from one and import it in another.

Figure 21. Group policy object security layout.
The security part of Group Policy supports additional security policies that are used in the Active Directory-based enterprise. These policies are also exposed under the Security Settings node in any group policy object (local or Active Directory-based). These include:
Internet Protocol Security Policy-This policy points to the IPSec policy object in the Active Directory. IPSec policy objects define encryption and signature requirements for IP packets between a source computer and various destination computers. For more information about IPSec, see the relevant white papers at https://www.microsoft.com
Public-key policies-These policies include several subpolicies that are used by Public Key Infrastructure-based technologies included in Windows 2000. These subpolicies include:
Using the ToolS |
To use the SCE, you must first load the snap-in into an MMC console.
To load SCE into the MMC console
Start MMC. From the Start menu, click Run. In the Open text box, type
Mmc.exe
Click Console, and then click Add/Remove Snap-ins.
Click Add.
Select Security Configuration Editor from the list, and click OK.
Click the Extensions tab. The drop-down list should say Security Configuration Editor.
Choose all of the listed extensions.
Return to the drop-down list to see if any new snap-ins appear. If so, select them one at a time and add their extensions.
Repeat the previous step until all extensions are added. This creates an MMC console with a fully loaded SCE.
Click Console, and then click Save As to save the console for future use.
Example 1: To customize redefined configurations
Start the saved SCE console.
Open the SCE node. You should see the default search path for configurations under your system directory.
Open that node, and you see the list of predefined configurations. The description associated with each configuration describes what you can do with a particular configuration.
Click Basic Security configuration.
Click Local Policies, and then click Security Options.
Click Rename Administrator account to.
Uncheck the box to enable the setting.
Enter a generic name such as "nobody."
Repeat the process with Rename Guest account name to. You can customize anything else in the configuration in this way.
Right-click the Base Security node, and select Save As.
In the File Open dialog box, provide a path name where you want to save this configuration.
Example 2: To create a new configuration
Start the saved SCE console.
Right-click the SCE node, and click Add configuration Search Path.
Browse to the directory where you want to keep your new configuration.
Click OK.
A node to the selected path is added under SCE node.
Right-click that node, and choose New Configuration.
A new node representing the configuration appears under that node. This configuration is completely blank. You can choose to do any of three things to fill this configuration:
To use SCM, you must first load the snap-in into an MMC console.
To load SCE into the MMC console
Start MMC. From the Start menu, click Run. In the Open text box, type
Mmc.exe
Click Console, and then click Add/Remove Snap-ins.
Click Add.
Select Security Configuration Manager from the list, and click OK.
Click the Extensions tab. The drop-down list should say Security Configuration Manager.
Choose all the listed extensions.
Go back to the drop-down list to see if any new snap-ins appear. If so, select them one at a time, and add their extensions.
Repeat the previous step until all extensions are added. This creates an MMC console with a fully loaded SCM.
Click Console, and then click Save As to save the console for future use.
Example 1: To apply a predefined configuration to the computer
Start the saved SCM console. By default, the scope is set at the local computer policy database.
Right-click the SCM node, and then click Import Configuration.
Use the File Open dialog to find the configuration you want to apply.
Ensure that the checkbox to overwrite existing configuration is not checked so that existing configuration is not overwritten unless specified in the configuration being imported.
Click OK. This makes the selected configuration part of stored configuration in local computer policy.
Select Configure Now from the SCM Context menu.
Example 2: To ensure that the system is consistent with the local computer policy database
Start the saved SCM console. By default, it is focused at the local computer policy database.
Right-click the SCM node, and click Analyze.
Provide the Error Log file path, and click OK.
The progress dialog showing the ongoing progress of analysis comes up.
If there are errors, Notepad starts with the log file in it to show any errors.
You can now navigate through various areas, for example, account policies, local policies, and so on and find any discrepancies that may exist. In a typical case, there are none.
Example 3: To export the current system configuration on one computer and reapply it on another system
Start the saved SCM console on the chosen computer. By default it is focused on the local computer policy database.
Right-click the SCM node, and click Export Configuration.
Provide the configuration file path where the configuration should be written. This may be a network path to some shared location. The configuration is written there when done.
To apply it to different computers, you have several possible choices:
Example 4: To analyze a system against configurations provided by an external source
Start the saved SCM console on the computer.
Right-click New Database, and select a new security database.
Right-click Import Configuration, and provide one of the configuration files.
Repeat the previous step for each configuration that should be included.
Right-click Analyze. Provide the error log file path, and click OK.
The progress dialog shows you what is occurring. Once it is completed, you can navigate to various areas and look for discrepancies. They are clearly identified by the X icons.
Example 1: To work with local computer policy
Right-click the My Computer icon on the desktop.
Click Manage. This starts the Computer Management snap-in.
On the System Tools menu, point to Local Computer Policy, point to Computer Settings, then select Security Settings. You should see the Security Configuration node. You can edit various policies, such as password, lockout, auditing, or user rights. These changes take effect immediately after you have completed all the changes and closed the snap-in.
Note: If you are in a domain-based group policy infrastructure, any changes that you make may be overwritten by changes from the Active Directory.
Example 2: To define account policies for the domain and all computers in that domain
Start the Active Directory Manager.
On the Start menu, point to Programs, then point to Administrative Tools, and then Active Directory Manager.
Right-click the Domain node, click Tasks; and then click Manage Group Policy.
The Group Policy assignment dialog box appears. It shows you all the existing GPOs assigned.
Click the Default Domain Account Policy GPO, and then click Edit.
This invokes the Group Policy Editor focused at the selected policy.
Click the Policy node. On the Computer Settings menu, point to Security Settings, and then click Account Policies.
Now you can open each node under account policies.
Example 3: To disable RAS, DHCP, and DNS on all computers in the domain except specific ones
There are two parts to configuring this policy. First
you should set up a generic top-level policy to disable these services on all
computers in the domain. Second, you should move specific computers that run
RAS, DHCP, and DNS into separate organizational units and configure the policy
to enable the corresponding service.
Part 1: To set up the generic top-level
policy
Start the Active Directory Manager. From the Start menu, point to Program Files, point to Administrative Tools, then click Active Directory Manager.
Right-click the Domain node, click Tasks, and then click Manage Group Policy. The Group Policy assignment dialog appears. It shows you all existing GPOs that are assigned.
Click Add. This starts the GPO assignment dialog box.
Click the New Group Policy option, and replace the name provided with the name Disable Network Services.
This creates the GPO and starts the GPE focussed on that GPO.
From the Computer Settings menu, point to Security Settings, and then click System Services.
Select each of the three services, and double-click to start the configuration dialog box.
Set the Service Startup Mode to Disabled, and click OK.
Close the snap-in. This configures the needed policy.
Part 2: To move RAS, DHCP, and DNS computers into separate organizational units and configure the policy to enable the corresponding service
Start the Active Directory Manager. From the Start menu, point to Program Files, point to Administrative Tools, then click Active Directory Manager.
Navigate to the location where you want to create the organizational unit to house computers running RAS servers. Click New, and then click Organizational Unit and type in the following name:
Remote Access Servers
Select the RAS OU. Right-click Tasks, and click Manage Group Policy. The Group Policy assignment dialog box appears.
Click Add. This starts the GPO assignment dialog box.
Select the New Group Policy option, and insert Enable RAS. This creates the GPO and invokes the GPE on that GPO.
From the Computer Settings menu, click Security Settings, then click System Services.
Select RAS Service, and double-click to start the configuration dialog box.
Set the service startup mode to Enabled, and click OK.
Close the snap-in. This configures the needed policy for RAS servers.
Repeat the above steps for DHCP and DNS servers.
For More Information |
For the latest information on Windows NT Server and Windows 2000, visit the Web site at https://www.microsoft.com/ntserver or the Windows NT Server Forum on the Microsoft Network (GO WORD: MSNTS).
Appendix A. Implementing Security Attachments |
This appendix describes the procedures for building and implementing attachments for the Security Configuration Tool Set.
Security attachment architecture requires implementation of the following two pieces:
An attachment engine DLL that implements three interfaces (described later in this appendix).
A Microsoft Management Console (MMC) extension snap-in that provides the configuration editor and manager functionality used to configure and analyze attachment-specific security settings. This extension may be exposed as a node at one of two possible places in the Security Configuration Tool Set name space:
Under the Services security area in the Security Configuration Editor and Manager snap-ins. This should be used when the attachment implements service-specific security configuration or analysis.
The Security Configuration Tool Set handles general security settings for individual services directly. These general settings include the service invocation policy (disabled, automatic, or manual), as well as the security descriptors for each service. Therefore, no security configuration attachment should attempt to configure these settings. The service security attachment architecture within the Security Configuration Tool Set provides an infrastructure to configure and analyze service-specific security settings for individual services. For example, Spooler is a Windows NT service that defines private objects (in this case, printers) that need to be secured. In addition, it has configuration parameters that are security-sensitive. For Spooler, a service security attachment must allow configuration and analysis of security settings on printer objects and security-sensitive parameters for the service.
At the same level as Services and other security areas. This should be used when the attachment implements a more general security configuration or analysis. For example, an attachment that tracks service packs and hot fixes applied to the system would be placed at this level since it applies to the entire system.
Security Configuration Tool Set provides a set of callback support APIs that the attachment engine or extension snap-in can use to query or set service-specific information contained in the security configuration and analyses database.
Figure 1A shows the pieces of the snap-in architecture where the attachment infrastructure fits in (the extension snap-ins for attachments, the attachment engines, and the inspection database).
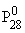
Figure 1A. Security Configuration tool set snap-in, engine, and extension architecture
The Security Configuration Tool Set, which consists of the main engine and the MMC snap-in, provides the overall framework for configuring and analyzing system security for installations of Windows NT and Windows 2000.
In the attachment framework, attachment engine DLLs register with the security configuration engine. The security configuration engine service then loads the attachment during execution. It calls the attachment's configuration interface when the system is configured, the analysis interface when the system is analyzed, and the update interface when parameters in the database are modified by the extension snap-in.
Similarly, the extension snap-in for the attachment must register as a Security Configuration Tool Set snap-in extension. The Security Configuration Tool Set snap-ins load the extension snap-in as a node under the Services security area or at the same level as the services area (based on how the extension registered) in both the editing and manager tools. If you are writing an extension snap-in, you must follow the MMC extension writer's documentation to implement the overall extension snap-in. In addition, you must implement the component object model (COM) interface described below to communicate with the Security Configuration Editor or Manager snap-ins.
Building the attachment involves implementing three interfaces and installing and registering the attachment with the Security Configuration Tool Set. The Security Configuration Tool Set loads the attachment, and then calls these interfaces, based on user-invoked operations.
Before describing which interfaces need to be implemented and how to implement them, it is important to define various data structures and supported APIs provided by the Security Configuration Tool Set.
Note that the data structures described here are declared in the Scesvc.h header file, included in the Microsoft Platform SDK.
SCE status codes-Various Security Configuration Tool Set status codes returned by helper functions and expected from the attachment interfaces.
typedef DWORD SCESTATUS;
#define SCESTATUS_SUCCESS 0L
#define SCESTATUS_INVALID_PARAMETER 1L
#define SCESTATUS_RECORD_NOT_FOUND 2L
#define SCESTATUS_INVALID_DATA 3L
#define SCESTATUS_OBJECT_EXIST 4L
#define SCESTATUS_BUFFER_TOO_SMALL 5L
#define SCESTATUS_PROFILE_NOT_FOUND 6L
#define SCESTATUS_BAD_FORMAT 7L
#define SCESTATUS_NOT_ENOUGH_RESOURCE 8L
#define SCESTATUS_ACCESS_DENIED 9L
#define SCESTATUS_CANT_DELETE 10L
#define SCESTATUS_PREFIX_OVERFLOW 11L
#define SCESTATUS_OTHER_ERROR 12L
#define SCESTATUS_ALREADY_RUNNING 13L
#define SCESTATUS_SERVICE_NOT_SUPPORT 14L
SCE handles-The opaque handles provided by the Security Configuration Tool Set to attachment interfaces for support of callback functions.
typedef PVOID SCE_HANDLE;
typedef ULONG SCE_ENUMERATION_CONTEXT, *PSCE_ENUMERATION_CONTEXT;
typedef struct _SCESVC_CALLBACK_INFO_ SCESVC_CALLBACK_INFO, *PSCESVC_CALLBACK_INFO;
SCE service configuration information-The information structure to be used by attachment interfaces when querying or setting configuration information to the database or configuration through the supported callback interfaces.
typedef enum _SCESVC_INFO_TYPE SCESVC_INFO_TYPE;
typedef struct _SCESVC_CONFIGURATION_LINE_ SCESVC_CONFIGURATION_LINE, *PSCESVC_CONFIGURATION_LINE;
typedef struct _SCESVC_CONFIGURATION_INFO_ SCESVC_CONFIGURATION_INFO, *PSCESVC_CONFIGURATION_INFO;
SCE service analysis information-The information structure to be used by attachment interfaces when querying or setting analysis information to the database through the support callback interfaces.
typedef enum _SCESVC_INFO_TYPE SCESVC_INFO_TYPE;
typedef struct _SCESVC_ANALYSIS_LINE_ SCESVC_ANALYSIS_LINE, *PSCESVC_ANALYSIS_LINE;
typedef struct _SCESVC_ANALYSIS_INFO_ SCESVC_ANALYSIS_INFO, *PSCESVC_ANALYSIS_INFO;
Security Configuration Tool Set provides a set of callback and support functions that the attachment should use to read or write information to the configuration file and the database.
These functions are:
PFSCE_QUERY_INFO-This callback function allows the attachment to obtain configuration or analysis information from the database for a service.
PFSCE_SET_INFO-This callback function lets the attachment set configuration or analysis information in the database for a given service.
PFSCE_FREE_INFO-This callback function should be used to free buffers allocated by the Security Configuration Tool Set for the attachment.
PFSCE_FREE_INFO-This callback function is used to write information to the log file generated during various SCTS operations: configuration, analysis, and policy propagation.
ConvertSecurityDescriptorToStringSecurityDescriptor-This function takes a binary self-relative Windows NT security descriptor and returns a text representation for it. This is useful for storing security descriptors in configuration files.
ConvertStringSecurityDescriptorToSecurityDescriptor-This function takes a text form security descriptor that was originally generated through ConvertSecurityDescriptorToStringSecurityDescriptor and returns a self-relative binary Windows NT security descriptor that represents it. This is useful in reading a textual security descriptor from a configuration file and applying it to an object on the system.
The callback functions are declared in the Scesvc.h header file in the Platform SDK and support functions are declared in the Sddl.h header file. The static libraries to link to are Scesvc.lib and Advapi32.lib, available for x86 and Alpha platforms. These functions are described in greater detail below.
PFSCE_QUERY_INFO
This callback function allows the attachment to query configuration or analysis information from the database.
typedef
SCESTATUS
(*PFSCE_QUERY_INFO)(
IN SCE_HANDLE sceHandle,
IN SCESVC_INFO_TYPE sceType,
IN LPTSTR lpPrefix OPTIONAL,
IN BOOL bExact,
OUT PVOID *ppvInfo,
OUT PSCE_ENUMERATION_CONTEXT psceEnumHandle
sceHandle-Opaque SCE handle passed to the attachment by the Security Configuration Tool Set. This is used to determine where the information is stored.
sceType-Must be SCE_SERVICE_CONFIGURATION_INFO if configuration information is being queried, or SCE_SERVICE_ANALYSIS_INFO if analysis information is being queried.
lpPrefix-May be NULL. If it is NULL, all keys are returned. If a string is supplied, information returned contains all keys (and corresponding values) with the same prefix as the specified string.
bExact-Not used if lpPrefix is NULL. If this parameter is TRUE, the key that matches exactly with the specified string in lpPrefix is returned. If this parameter is FALSE, all keys (and their values) that have the same prefix as the specified string in lpPrefix are returned.
ppvInfo-Pointer to a pointer of type SCESVC_CONFIGURATION_INFO if sceType is SceSvcConfigurationInfo. Otherwise, it must be SCESVC_ANALYSIS_INFO if sceType is SceSvcAnalysisInfo. The Security Configuration Tool Set-and not the attachment-allocates the buffer; therefore the pointer must point to NULL.
psceEnumHandle-Handle that must be used in successive calls to this function. The function may not return all the keys in a single call because there could be large number of keys. (The maximum number of keys returned in a single call is 256.)
SCESTATUS_SUCCESS indicates success. One of the following indicatues failure:
SCESTATUS_INVALID_PARAMETER
SCESTATUS_RECORD_NOT_FOUND
SCESTATUS_BAD_FORMAT
SCESTATUS_OTHER_ERROR
SCESTATUS_NOT_ENOUGH_RESOURCE
PFSCE_SET_INFO
This callback API allows the attachment to set/overwrite configuration/analysis information stored in the database about a particular service.
typedef
SCESTATUS
(*PFSCE_SET_INFO)(
IN SCE_HANDLE sceHandle,
IN SCESVC_INFO_TYPE sceType,
IN LPTSTR lpPrefix OPTIONAL,
IN BOOL bExact,
IN PVOID pvInfo
Parameters
SceHandle-Opaque handle that the Security Configuration Tool Set passes to the attachment. This is used to determine where the information is stored.
SceType-This must be SCE_SERVICE_CONFIGURATION_INFO if configuration information is being set, or SCE_SERVICE_ANALYSIS_INFO if analysis information is being set.
lpPrefix-May be NULL. If it is NULL, all service information is overwritten with the supplied information. If a string is supplied, information overwritten contains all keys (and corresponding values) with the same prefix as the specified string.
bExact-Not used if lpPrefix is NULL. If this parameter is TRUE, the key that matches exactly with the specified string in lpPrefix is overwritten. If this parameter is FALSE, all keys (and their values) that have the same prefix as the specified string in lpPrefix are overwritten.
pvInfo-This must be a pointer of type SCESVC_CONFIGURATION_INFO if the sceType is SceSvcConfigurationInfo. Otherwise, it must be SCESVC_ANALYSIS_INFO if the sceType is SceSvcAnalysisInfo.
SCESTATUS_SUCCESS indicates success. One of the following indicates failure:
SCESTATUS_INVALID_PARAMETER
SCESTATUS_RECORD_NOT_FOUND
SCESTATUS_BAD_FORMAT
SCESTATUS_NOT_ENOUGH_RESOURCE
SCESTATUS_ACCESS_DENIED
SCESTATUS_DATA_OVERFLOW
SCESTATUS_OTHER_ERROR
PFSCE_FREE_INFO
The attachment must call this function to free buffers allocated by the Security Configuration Tool Set in calls to PFSCE_QUERY_INFO.
typedef
SCESTATUS
(*PFSCE_FREE_INFO)(
IN PVOID pvServiceInfo
pvServiceInfo -Pointer to the allocated buffer.
SCESTATUS_SUCCESS indicates success. SCESTATUS_INVALID_PARAMETER indicates failure.
PFSCE_LOG_INFO
The attachment can call this function to write information to the log file generated when the Security Configuration Tool Sset performs configuration, analysis and policy propagation on a system.
typedef
SCESTATUS
(*PFSCE_LOG_INFO)(
IN INT ErrLevel,
IN DWORD Win32rc,
IN LPTSTR pErrFmt,
...
ErrLevel Specifies the error log level at which the provided log information should be written to the log file. If the invoked operation is at that level, the attachment's information is logged, otherwise, it is ignored. The defined levels are:
#define SCE_LOG_LEVEL_ALWAYS 0
#define SCE_LOG_LEVEL_ERROR 1
#define SCE_LOG_LEVEL_DETAIL 2
#define SCE_LOG_LEVEL_DEBUG 3
Win32rc Return value that to be written to the log. This may be the error value returned by some system API called by the attachment to perform configuration or analysis.
PErrEmt The null-terminated string to be written to the log file.
ConvertSecurityDescriptorToStringSecurityDescriptor
This is a helper function that allows the attachment to convert a self-relative security descriptor into a textual form that can be stored in the configuration file and the database. This function is useful when an attachment is configuring security on a service that supports private objects that have security descriptors.
WINADVAPI
BOOL
WINAPI
ConvertSecurityDescriptorToStringSecurityDescriptorA(
IN PSECURITY_DESCRIPTOR SecurityDescriptor,
IN DWORD RequestedStringSDRevision,
IN SECURITY_INFORMATION SecurityInformation,
OUT LPSTR *StringSecurityDescriptor OPTIONAL,
OUT PULONG StringSecurityDescriptorLen OPTIONAL
);
WINADVAPI
BOOL
WINAPI
ConvertSecurityDescriptorToStringSecurityDescriptorW(
IN PSECURITY_DESCRIPTOR SecurityDescriptor,
IN DWORD RequestedStringSDRevision,
IN SECURITY_INFORMATION SecurityInformation,
OUT LPWSTR *StringSecurityDescriptor OPTIONAL,
OUT PULONG StringSecurityDescriptorLen OPTIONAL
);
SecurityDescriptor-Pointer to the security descriptor. (See the Platform SDK for functions that manipulate security descriptors.)
RequestedStringSDRevision-Specifies the revision level for security descriptor text representation. Must be SDDL_REVISION.
SecurityInformation-Specifies the security information part of the security descriptor that must be converted to textual form. (See the Platform SDK for value values of SECURITY_INFORMATION.)
StringSecurityDescriptor-Specifies the string form of the security descriptor returned by this function. The buffer is allocated by the function and must be freed using the SceSvcFree function when it is no longer needed.
StringSecurityDescriptorLen-Pointer to a ULONG that is filled with the length of the string.
The string to return the textual form is allocated by this helper function. It must be freed using the LocalFree function.
SCESTATUS_SUCCESS indicates success. One of the following indicates failure:
SCESTATUS_INVALID_PARAMETER
SCESTATUS_NOT_ENOUGH_RESOURCE
ConvertStringSecurityDescriptorToSecurityDescriptor
This is a helper function that allows the attachment to convert a textual form of a security descriptor (created earlier using ConvertSecurityDescriptorToStringSecurityDescriptor) back to its self-relative binary form.
WINADVAPI
BOOL
WINAPI
ConvertStringSecurityDescriptorToSecurityDescriptorA(
IN LPCSTR StringSecurityDescriptor,
IN DWORD StringSDRevision,
OUT PSECURITY_DESCRIPTOR *SecurityDescriptor,
OUT PULONG SecurityDescriptorSize OPTIONAL
);
WINADVAPI
BOOL
WINAPI
ConvertStringSecurityDescriptorToSecurityDescriptorW(
IN LPCWSTR StringSecurityDescriptor,
IN DWORD StringSDRevision,
OUT PSECURITY_DESCRIPTOR *SecurityDescriptor,
OUT PULONG SecurityDescriptorSize OPTIONAL
);
StringSecurityDescriptor-Specifies the text form of the security descriptor.
RequestedStringSDRevision-Specifies the revision level for the security-descriptor text representation. Must be SDDL_REVISION.
SecurityDescriptor-Pointer to a security descriptor pointer. This function allocates necessary memory to create the self-relative security descriptor. It must be freed using the SceSvcFree function when it is no longer needed.
SecurityDescriptorSize-Specifies the size of allocated security descriptor.
The buffer to return a security descriptor is allocated by this helper function. It must be freed using the LocalFree function.
SCESTATUS_SUCCESS indicates success. One of the following indicates failure:
SCESTATUS_INVALID_PARAMETER
SCESTATUS_RECORD_NOT_FOUND
SCESTATUS_NOT_ENOUGH_RESOURCE
The three interfaces that the attachment must implement are:
SceSvcAttachmentConfig-Security Manager calls this interface when the system is configured.
SceSvcAttachmentAnalyze-Security Manager calls this interface when the system is analyzed.
SceSvcAttachmentUpdate-Security Manager calls this interface when it receives a configuration update request from the MMC snap-in.
SceSvcAttachmentConfig
typedef
SCESTATUS
(*PF_ConfigAnalyzeService)(
IN PSCESVC_CALLBACK_INFO pSceCbInfo
PSceCbInfo-Structure passed to the attachment engine by the Security Cconfiguration Tool Set when this interface is invoked. It provides a context handle that is used by the various callback functions. It also provides the function pointers to the callback functions.
This interface must do the following:
Use the Security Configuration Tool Set support function PFSCE_QUERY_INFO to query configuration information.
Configure the service.
SCESTATUS_SUCCESS indicates success.
Any other return value defined above.
SCESTATUS
WINAPI
SceSvcAttachmentConfig(
IN PSCESVC_CALLBACK_INFO pSceCbInfo
)
// now read the information and configure system using it.
// NOTE: you may decide to read all the information first
// and then do the configure, it is implementor's choice.
do __except (EXCEPTION_EXECUTE_HANDLER)
if(retCode == SCESTATUS_SUCCESS &&
pConfigInfo != NULL)
//
// free the data we got back.
//
__try __except (EXCEPTION_EXECUTE_HANDLER)
PConfigInfo = NULL;
}
//
// handle other return codes, as needed.
//
} while ( retCode == SCESTATUS_SUCCESS && CountReturned > 0);
// if return code is not success, we should set up
// error message appropriately.
// return the retCode.
return retCode;
SceSvcAttachmentAnalyze
typedef
SCESTATUS
(*PF_ConfigAnalyzeService)(
IN PSCESVC_CALLBACK_INFO pSceCbInfo
PSceCbInfo-Structure passed to the attachment engine by the Security Cconfiguration Tool Set when this interface is invoked. It provides a context handle that is used by the various callback functions. It also provides pointers to the callback functions.
This interface must do the following:
Query configuration information from the service directly.
Use PFSCE_QUERY_INFO to query configuration information.
Compute the differences of the parameters based on type and syntax.
Use PFSCE_SET_INFO to write the differential information to the database.
SCESTATUS_SUCCESS indicates success.
Any defined SCESTATUS error values are accepted.
SCESTATUS
WINAPI
SceSvcAttachmentAnalyze(
IN SCE_HANDLE sceHandle,
OUT PWSTR *ppszErrMessage,
OUT PDWORD pdErrLength
// now read the base config information, query system
// setting corresponding to it, compare them
// and write to the database.
do __except (EXCEPTION_EXECUTE_HANDLER)
if(retCode == SCESTATUS_SUCCESS &&
pConfigInfo != NULL)
__except (EXCEPTION_EXECUTE_HANDLER)
if(retCode != SCESTATUS_SUCCESS)
}
}
//
// free the data we got back.
//
SceSvcFree((PVOID)pConfigInfo);
__try __except (EXCEPTION_EXECUTE_HANDLER)
PConfigInfo = NULL;
// should also free possible buffers SystemValue and
// Result, up to each attachment
}
//
// handle other return codes, as needed.
//
} while ( retCode == SCESTATUS_SUCCESS && pConfigInfo != NULL);
// if return code is not success, we should set up
// error message appropriately, if error buffer is not NULL
// return the retCode.
return retCode;
SceSvcAttachmentUpdate
The Security Configuration Tool Set (or Manager) calls this interface when the Security Configuration Editor (or Manager) snap-in passes service-specific changes to the configuration settings stored in the database.
typedef
SCESTATUS
(*PF_UpdateService)(
IN PSCESVC_CALLBACK_INFO pSceCbInfo,
IN PSCESVC_CONFIGURATION_INFO ServiceInfo
PSceCbInfo-Structure passed to the attachment engine by the Security Configuration Tool Set when this interface is invoked. It provides the context handle that is to be used in the various callback functions. It also provides the pointers to the callback functions.
ServiceInfo-Specifies updated configuration information, which is based on user edits and is supplied by the attachment's extension snap-in. (See the explanation of the SCESVC_CONFIGURATION_INFO data structure in the data structures section.)
This attachment interface must do the following:
Use PFSCE_QUERY_INFO to query the base information (configuration information) stored in the database.
Use PFSCE_SET_INFO to query the last set of differences (analysis information) stored in the database.
Use the ServiceInfo supplied to compute the new base configuration information.
Use the ServiceInfo supplied and the last stored differences to compute the new differential information.
Use PFSCE_SET_INFO to write the new base configuration information to the database.
Use PFSCE_SET_INFO to write the new differential information to the database.
SCESTATUS_SUCCESS indicates success.
Any valid SCESTATUS error values are accepted.
SCESTATUS
WINAPI
SceSvcAttachmentUpdate(
IN SCE_HANDLE sceHandle,
IN SCESVC_CONFIGURATION_INFO *ServiceInfo
);
//
// process each line of the passed information.
//
for(i=0; i < ServiceInfo->Count; i++)
__except (EXCEPTION_EXECUTE_HANDLER)
if(retCode != SCESTATUS_SUCCESS &&
retCode != SCESTATUS_RECORD_NOT_FOUND)
//
// if the value specified is NULL, deletion
// of the key is requested.
//
if(ServiceInfo->Line[i].Value == NULL)
__except (EXCEPTION_EXECUTE_HANDLER)
if(retCode == SCESTATUS_RECORD_NOT_FOUND)
__except (EXCEPTION_EXECUTE_HANDLER)
if(retCode != SCESTATUS_SUCCESS)
}
elseif (retCode == SCESTATUS_SUCCESS)
else
//
// delete the key
//
__try __except (EXCEPTION_EXECUTE_HANDLER)
if(retCode != SCESTATUS_SUCCESS)
}
//
// SCESTATUS_RECORD_NOT_FOUND means nothing more.
// as the key does not even exist.
//
}
else
if ( pConfigInfo != NULL ) __except (EXCEPTION_EXECUTE_HANDLER)
pConfigInfo = NULL;
if ( pAnaInfo != NULL ) __except (EXCEPTION_EXECUTE_HANDLER)
PAnalInfo = NULL;
}
//
// error cleanup
// set detail error message appropriately if the buffer
// is not NULL
//
return retCode;
The attachment DLL must be installed on the Windows NT or Windows 2000-based system where it is expected to be used. In addition, the Security Configuration Tool Set must be aware of the presence of the attachment.
To install and register the DLL
Copy the attachment DLL to a particular directory. The preferred directory is %windir%\Security\Attachments. You can create this directory if it does not already exist. Only system administrators are expected to install attachments on the system.
Create a registry key under:
HKEY_LOCAL_MACHINE\
Software\
Microsoft\
Windows NT\
CurrentVersion\
SecEdit\Services\
[Service Name]
The Service Name used here is the registered name for the attachment. It should be unique so it does not collide with other attachments. The service name must be the same name used in the Service Control Manager if the attachment configures service-specific settings. The name used in the Service Control Manager is the name to link each service with Security Configuration Tool Set.
Create the following values in this key:
The Security Configuration Tool set snap-ins are designed to be extensible to support the attachment extension snap-ins. Communication between the Security Configuration Tool Set snap-ins and the extension snap-ins is handled by the standard MMC mechanisms and two well-defined Component Object Model (COM) interfaces. The attachment engine is responsible for configuring and analyzing service security and updating the service configuration in the database; the attachment extension allows user to view, create, and modify configurations and analysis information. To function correctly, the attachment snap-in must follow the MMC extension snap-in guidelines and the attachment guidelines provided in this document.
Each attachment snap-in must be an extension snap-in, and these extension snap-ins provide functionality only when invoked by the Security Configuration Tool Set (or Manager) snap-in. Each attachment snap-in can extend only Services nodes. It declares itself subordinate to Services nodes , and then, for each occurrence of the Services node type, the MMC console automatically adds the related snap-in extensions. Each attachment owns one scope pane node and the related result pane in MMC. Attachment extensions must allow the user to create or modify service-security settings in a configuration managed by the Security Configuration Editor (and Manager) snap-in. It must also be able to display configuration and/or analysis security settings with analysis status. It must support editing of service configuration settings for a system, and the analysis results must be updated based on the updated configuration settings.
It is up to the attachment extension to determine the format and implementation logic of its own result pane. COM interfaces provide a way to extend Security Configuration Editor (and Manager) functionality for services, without dictating how each service extension performs its particular tasks. See the COM interface layout shown in Figure A2.
Figure A2. COM interface layout for attachment
In this illustration, the Security Configuration Editor (or Manager) Snap-in implements the ISceSvcAttachmentData interface. The interface provides the attachment snap-in to query configuration and analysis information from configurations or the database. The attachment snap-in implements the ISceSvcAttachmentPersistInfo interface, which is used by the Security Configuration Editor (or Manager) snap-in to get any modified information that may need to be written to the configuration or the database. The snap-in then saves this information appropriately.
There are three operations that the attachment snap-in must support:
Display configuration and/or inspection information-To display information, the attachment snap-in node extends the Security Configuration Editor (or Manager) snap-in through the Services node. The Security Configuration Editor (or Manager) node types that can be extended are:
When creating or editing a configuration, if the services node is expanded, all registered extension snap-ins are notified by the MMC directly. Each attachment should insert itself under the Services node, and then complete the following steps:
Use the QueryInterface method to query the ISceSvcAttachmentData interface.
Call the Initialize method to inform the Security Configuration Tool Set that it is loaded and establish a context to communicate for appropriate information.
Either use the GetData method to pull information immediately or wait until its node is selected by the user.
Modify configuration information in the configurations-The attachment snap-in must allow the user to modify configuration information about the service. The modified information must be held by the attachment snap-in until the Security Configuration Editor (or Manager) uses the ISceSvcAttachmentPersistInfo interface to pull the information. To avoid memory leaks, memory allocated is freed by the owner. For this reason, both interfaces have a FreeBuffer method.
Modify configuration information in the database-The attachment snap-in must also support modifications to configuration information through the inspection node. This allows the user to make changes and reapply the configuration. The logic to do this should be identical to modifying information in the configuration files. The changes made take effect on the saved configuration in the inspection database.
#define CCF_SCESVC_ATTACHMENT ( L"CCF_SCESVC_ATTACHMENT" )
This clipboard is used for each attachment snap-in to extract the configuration file name from the Security Configuration Editor (or Manager). The configuration file name is a PWSTR. This configuration name is used in further communications between the attachment and the Security Configuration Editor (or Manager) in the Initialize method.
The extension snap-in queries the following Security Configuration Editor (or Manager) snap-in interfaces.
ISceSvcAttachmentData
This interface is implemented by the Security Configuration Editor (or Manager) snap-in to support extension snap-ins. The attachment extension snap-in should use it to retrieve service-specific information for display user modification.
class ISceSvcAttachmentData : public IUnknown
ISceSvcAttachmentPersistInfo
This interface is an abstract class that must be implemented by each attachment extension snap-in. The Security Configuration Editor (or Manager) snap-in calls this interface to check if there is modified information that must be written back to the configuration file or the database (using IsDirty). If that is the case, it calls the Save method to make the extension snap-in communicate the information that must be saved.
class ISceSvcAttachmentPersistInfo : public IUnknown
The Security Configuration Editor (or Manager) snap-in provides extensions only through the Security Configuration Editor (or Manager) name space. Context menus, toolbars, toolbar buttons, and property pages are not extensible at this point. The attachment snap-in must extend the Security Configuration Editor (or Manager) name space by populating its own node at well-defined places in the name space.
Attachment snap-ins should be registered under the registry key:
HKEY_LOCAL_MACHINE\
Software\
Microsoft\
MMC\
Snapins
The StandAlone key should not be created under the snap-in because each attachment snap-in must be an extension only.
Attachment snap-ins must also register themselves under the Security Configuration Editor Services NodeType subkeys as follows:
To extend the Security Configuration Editor name space, use the registry key:
HKLM\
Software\
Microsoft\
MMC\
NodeTypes\
24a7f717-1f0c-11d1-affb-00c04fb984f9\
Extensions\
NameSpace
To extend the Security Configuration Manager inspection (analysis) name space, use the registry key:
HKLM\
Software\
Microsoft\
MMC\
NodeTypes\
678050c7-1ff8-11d1-affb-00c04fb984f9\
Extensions\
NameSpace
For more information, refer to the Scesvc.h header file in the Platforms SDK.
To register the attachment snap-ins as extensions to the Security Configuration Editor or Manager snap-in, create these keys in your DllRegisterServer and DllUnregisterServer function implementations.
When a Services node under either the Security Configuration Editor or the Security Configuration Manager is expanded, MMC uses IComponentData::Notify and the MMCN_EXPAND event to notify the Security Configuration Editor or Manager and all of its extensions. The Security Configuration Tool Set then extracts its internal format from the lpDataObject and stops further processing when it sees the Services node type. The attachment snap-ins (registered as extensions) also extract the node type from the lpDataObject. If the node type is one of the Services node types defined earlier, the attachment snap-ins insert their root nodes under the specified parent node.
// detect which extension node to extend
GUID* nodeType = ExtractNodeType(lpDataObject);
if ( nodeType == NULL )
if ( ::IsEqualGUID(*nodeType, cNodetypeSceTemplateServices) == TRUE )
folderType =ATTACHEMNT_STATIC; // defined by attachment writer.
else if (::IsEqualGUID(*nodeType, cNodetypeSceAnalysisServices)
== TRUE)
folderType =ATTACHMENT_STATIC_ANALYSIS;
// defined by attachment writer
// Free resources
::GlobalFree(reinterpret_cast<HANDLE>(nodeType));
// As an extension snapin, the service attachment
// root node should be added
// Insert that node, and remember it
// as the root of the SMB Extension namespace.
CheckAndInsertRootNodeToMMCScopePane
The next major step in the initialization is to establish communication with the Security Configuration Editor or Manager snap-in. This is necessary because the attachment gets its data, as well any changes made by the user, from the Security Configuration Editor or Manager. To do this, follow these steps:
Obtain the configuration name. If the Services node type that the attachment is inserted under was that of a configuration, the attachment needs to know which configuration it is. It communicates this information to the Security Configuration Editor or Manager during interface initialization. The configuration name can be obtained through the clipboard format, as follows:
PWSTR * TemplateName = ExtractTemplateNameFromDataObject(lpDataObject);
Set up the context with the Security Configuration Editor or Manager. Once the configuration name is known (or if the Service node is of type Inspection), the attachment snap-in must query the ISceSvcAttachmentData interface and call the Initialize method to set up the context.
// QueryInterface for the main snap-in's IUnkown.
LPUNKNOWN pUnk;
hr = lpDataObject->QueryInterface(IID_IUnknown,
reinterpret_cast<void**>(&pUnk));
// QueryInterface ISceSvcAttachmentData
if ( SUCCEEDED(hr) )
// QueryInterface the attachment's IUnknown as
// that is needed by the main snap-in.
((LPUNKNOWN)m_pSnapin)->QueryInterface(IID_IUnknown, reinterpret_cast<void**>(&pUnk));
// Call Initialize to setup context with main snap-in.
m_pSceData->Initialize(ServiceName, TemplateName, pUnk, &sceHandle);
Note You must call CloseHandle to close the sceHandle once you are done.
Get the appropriate data. The attachment snap-in can use the established context to query appropriate data from the Security Configuration Editor, as needed, by using the GetData interface. The attachment may decide to do this proactively as soon as it initializes with the Security Configuration Editor, or it may wait until the user actually attempts to expand the attachment node by clicking it. The attachment can display the information received using any UI controls available.
// GetData - we get the configuration information here.
m_pSceData->GetData (sceHandle, SceSvcConfigurationInfo, &pData,
&enumHandle );
Note You must use the FreeBuffer method to free the buffer allocated by Security Configuration Editor or Manager.
After initialization, it is important that the attachment implement the ISceSvcAttachmentPersistInfo interface. The Security Configuration Editor or Manager queries this interface at various times, as when saving the configuration and when closing the snap-in, to allow the attachment to save any modifications that the user may have made to the inspection database or to the associated configuration.
class CSceSvcAttachmentPersistInfo:
public ISceSvcAttachmentPersistInfo,
public CComObjectRoot
// Implementing IsDirty()
STDMETHODIMP CSceSvcAttachmentPersistInfo::IsDirty()
//
// just calling the snapin's main IsDirty.
//
return m_pSnapin->IsDirty();
// Implementing Save()
STDMETHODIMP CSceSvcAttachmentPersistInfo::Save(
SCE_HANDLE *psceHandle,
PVOID *ppvData,
PBOOL pbOverwriteAll )
if ( m_pSnapin != NULL )
return S_OK;
// Implementing FreeBuffer
STDMETHODIMP CSceSvcAttachmentPersistInfo::FreeBuffer(PVOID pvData)
PSCESVC_ANALYSIS_INFO pTempInfo=(PSCESVC_ANALYSIS_INFO)pvData;
if ( pTempInfo->Lines != NULL )
LocalFree( pTempInfo->Lines);
}
LocalFree(pTempInfo);
return S_OK;
|