Microsoft® Corporation
Published: February 2007
Purpose
This guide provides an overview of various features of the Volume Activation Management Tool (VAMT) and provides prescriptive guidance on how to perform MAK Independent and MAK Proxy activation of Windows Vista and Windows Server codename "Longhorn" computers using a Multiple Activation Key (MAK).
Who Should Use the Volume Activation Management Tool?
This guide is targeted at IT professionals who are responsible for deploying and managing MAK activations for Windows VistaT or Windows Server codename "Longhorn" computers.
Information in this document, including URL and other Internet Web site references, is subject to change without notice.
Unless otherwise noted, the companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted in examples herein are fictitious. No association with any real company, organization, product, domain name, e-mail address, logo, person, place, or event is intended or should be inferred.
Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation.
Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property.
© 2007 Microsoft Corporation. All rights reserved.
Microsoft, Active Directory, ActiveX,
Windows, Windows 2000, Windows Server, Windows Vista, and Windows XP
are either registered trademarks or trademarks of Microsoft Corporation in the
The names of actual companies and products mentioned herein may be the trademarks of their respective owners.
Contents
Volume Activation Management Tool
Volume Activation 2.0 Solution
Benefits of Volume Activation 2.0
Volume Activation Management Tool Overview
Volume Activation Management Tool Scenarios
Volume Activation Management Tool Privacy Statement
Software asset and license management pose continual challenges for both enterprise customers as well as software developers. The issue of genuine software (running legitimately licensed operating systems and applications as opposed to illegitimate software) not only impacts the software vendors but the consumers, corporate users and partners. Yankee group (sponsored by Microsoft) in its research concluded that consumers and businesses that deploy counterfeit software put themselves, their end users, business partners and suppliers at serious risk for:
Network downtime and lost data increases when the counterfeit software malfunctions.
Technical service and support and interoperability issues involving counterfeit software typically take longer to resolve because either the gray market source is long gone or the legitimate software vendor will spend more time trying to troubleshoot.
Businesses that knowingly or unwittingly use counterfeit software are at increased risk of litigation from business partners, suppliers and customers in the event their network operations are adversely affected when something goes awry with the pirated software.
Non-genuine software also raises the risk of incompatibility with legitimate Windows and Office patches, fixes and updates.
Research by IDC (sponsored by Microsoft) shows that acquiring and using counterfeit software can pose real risks. The research examined websites that offer counterfeit software as well as hacks, cracks and 'keygen' tools available on websites and P2P networks that enable the illegal use of software. The research found there is a significant amount of malicious or unwanted code present in key generators and crac 14114v2121o k tools, and on websites that offer counterfeit software. Specifically, malicious or unwanted software was found in:
25% of the Web sites (25 of 98 sites) offering counterfeit product keys, pirated software, key generators or crack tools
11% of key generators and crac 14114v2121o k tools (13 out of 116) downloaded from websites
59% of key generators and crac 14114v2121o k tools (55 of 94) downloaded from P2P networks
Finally the previous versions of Microsoft
Windows didn't provide tools and solutions to enterprise customers that are
necessary to protect and manage the software and the associated license
keys.
For these reasons, Microsoft continually invests in technologies and programs to help protect consumers and businesses from the risks and hidden costs of counterfeit and unlicensed software while enabling the enterprise customers in their software asset and license management efforts.
Volume Activation 2.0 is a new requirement in the Windows VistaT and Windows Server® Code Name "Longhorn", which requires activation of each Windows Vista license acquired under a Volume License agreement. When designing and building the new volume activation technologies, Microsoft focused on the following goals:
Close significant piracy loopholes (Volume License keys represent the majority of the keys that are involved in Windows piracy.)
Enable protection and management of volume license keys with minimal impact to deployment and management of the infrastructure
Improve the customer experience
Volume Activation 2.0 is designed to help increase protection and to help better manage the Volume License keys in managed and non-managed environments as well as provide flexible deployment options for customers. The process is transparent for end users, and the Volume Activation 2.0 solution works in a variety of customer environments.
Volume Activation 2.0 supports centrally managed Volume License keys. The Key Management Service (KMS) key used for KMS activation is only installed on the KMS host and never on individual computers. The Multiple Activation Key (MAK), although resident on the individual computer, is encrypted and kept in a trusted store so that users are not exposed to the key and are not able to obtain the key once it has been installed on the computer.
Volume Activation 2.0 supports a simplified setup and is generally invisible to the customer. By default, Volume editions do not require a product key to be entered during setup. The computer must be activated during an automatic 30-day grace period.
System Administrators can count KMS activations using standard system management software including the Microsoft Operations Manager (MOM), as well as the Volume Activation Management Tool (VAMT). Windows Management Infrastructure (WMI), extensive event logging, and built-in Application Programming Interfaces (APIs) may provide a wealth of detail about installed licenses and about the license state and current grace or expiration period of MAK and KMS-activated computers.
Volume Activation 2.0 may provide enhanced security through frequent background validations for genuine modules. This is currently limited to critical software, but may be expanded over time.
The Volume Activation Management Tool (VAMT) enables organizations to optimize their desktop deployment infrastructure with features such as performing MAK proxy activation, reporting on the activation status of all machines in the environment, and returning current MAK activation count(s). This tool is designed to run as a stand-alone application on any Windows machine (Windows XP, Windows Server 2003, or Windows Vista). VAMT enables IT pros to automate and centrally manage the volume activation process using MAK Key:
MAK independent activation - Many enterprises maintain a single system image for deployment across the enterprise. MAK independent activation enables enterprise customers to distribute a MAK key to one or more connected computers within their network and to optionally instruct those computers to activate over the Internet immediately.
MAK proxy activation - This activation method is designed for environments that preclude direct access to the Internet- where the only current method of activation is phone activation. MAK proxy activation enables enterprise customers to acquire and send a list of installation IDs to the Microsoft activation clearinghouse. The proxy retrieves the corresponding confirmation IDs and distributes them to the client computers. Additionally, export/import functionality enables activation in a disconnected environment.
VAMT is designed to manage MAK activation for computers running Microsoft Windows Vista or Windows Server codename "Longhorn". Computers running volume editions of Microsoft Windows XP or Windows Server 2003 cannot be managed using VAMT.
VAMT features are detailed in the VAMT.CHM and listed below.
Adding Computers - Discovering and grouping computers from the local environment. VAMT can discover computers by querying Active Directory, Workgroups, or by individual computer name or IP address.
Status Collection and Reporting - VAMT collects information on listed computers including the product key being used, the current license state (Licensed, Grace, and Unlicensed), the Operating System and the edition of Windows being run.
MAK Management - VAMT stores one or more MAKs in the Computer Information List (CIL) file. This allows the user to query the Activation database to determine the number of activations remaining for their organizations MAKs. The CIL is a XML file, and readable with any TEXT editor such as Notepad. Administrators should ensure that CIL files are stored securely.
MAK Independent Activation - This process applies a MAK to selected computers and allows them to self-activate via the Internet. Selected computers can also be instructed to activate immediately.
MAK Proxy Activation - The MAK Proxy Activation extracts the IID from selected computers. That IID is transmitted to Microsoft's activation servers. The VAMT host receives a CID - the Confirmation ID - for each IID submitted. These CIDs are matched up with the IIDs and other information on the VAMT host, and the CIDs are installed to the proper client computers, activating them.
Importing and Exporting Data - VAMT stores data in a CIL (Computer Information List) file, in XML format. VAMT can export this data for transport to other VAMT hosts or for archival. The Exported CIL contains all the data necessary for MAK Proxy Activation. The CIL can be imported on a separate VAMT host, allowing systems to be Proxy activated in bulk without direct connection to the Internet. A primary use for this technology is support for isolated, high-security networks. For cases in which security is paramount, the Export can be restricted to only non-PII (Personally Identifiable Information). Likewise, VAMT can import CIL files: the computer records in the CIL can be presented to Microsoft for a corresponding CID, or the data can be merged with existing computer groups. This is useful for archiving the Computer groups and status, as well as recording the CIDs for reuse, and is a necessary step in MAK Proxy Activation. A secure export containing non-PII data must be merged into a full saved CIL file in order for VAMT to correctly match IID/CID to computer names.
VAMT v1.0 is only available in an EN-US (x86) version and includes a CHM file which provides details on various VAMT features.
Step 14: Reimaging Scenario for Isolated Labs (OPTIONAL) in the VAMT.CHM is incorrect. Specifically, Installing a MAK on a computer will write an IID in the CIL file and also delete the CID, if it exists. The solution in the Reimaging Scenario is to reopen the existing CIL file before selecting Apply Confirmation ID as documented below
This section illustrates the use of MAK activation and the Volume Activation Management Tool (VAMT) in two scenarios:
MAK Independent Activation
MAK Proxy Activation
The following diagram depicts several environments common to large organizations. This guide details the use of VAMT to activate Vista Volume Edition computers in the Core Network and Isolated Lab environments shown below.
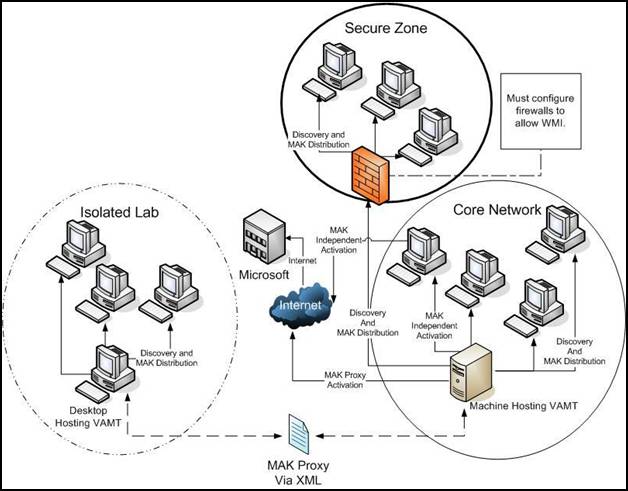
Figure1: Sample Network
In this scenario VAMT is deployed in the Core Network environment shown in the diagram above. In the Core Network environment, all computers are on a common network managed by Active Directory. VAMT is installed on a central computer with network access to all client computers. Both the VAMT host and client computers have access to the Internet.
Step 1: Install and launch VAMT
Step 2: Configure WMI Firewall Exception on Target Computers
Step 3: Add computers to the Computer Information List (CIL)
Step 4: Collect Status for the Discovered Computers
Note: To retrieve the licensing status on the selected computers, VAMT must have administrative permissions on the remote computers, WMI must be accessible through the Windows firewall, and for workgroup computers a registry key must be created to enable remote administrative actions under User Account Control (UAC). See Client Configuration for more details.
Step 5: Enter a MAK Key and Determine its Activation Capacity
Step 6: MAK Independent Activation
The computers in the Core Network group should all be activated as MAK clients.
Note: Selecting the Install MAK (overwrite existing) checkbox will force installation of the MAK. This must be done with care. If the computer has run for more than 30 days, then its Initial Grace period has expired and it will be put into Reduced Functionality Mode (RFM) if MAK Independent Activation is not completed successfully before the next logon. VAMT can be used to recover properly configured remote computers from RFM as long as they are accessible on the network.
MAK proxy is usually performed in environments that have more constraints than the core network, above. Use MAK Proxy Activation for Isolated Lab environments that do not have direct access to the Internet. In this scenario VAMT is deployed to the Isolated Lab environment shown in the diagram above. This environment is physically separate from the rest of the network and the computers are members of a workgroup. The Network Security Policy states that no information can be transferred out of the Isolated Lab that could identify a specific computer or user.
Step 1: Install and launch VAMT on a computer in the Isolated Lab
Note: This scenario assumes that a second VAMT host with Internet access exists outside of the Isolated Lab.
Step 2: Configure WMI Firewall Exception on Target Computers
Step 3: Add computers to the Computer Information List (CIL)
Note: For VAMT to discover client computers in a workgroup, the Windows firewall exception "Network Discovery" must be enabled.
Step 4: Collect Status for the Discovered Computers
Note: To retrieve the licensing status on the selected computers, VAMT must have administrative permissions on the remote computers, WMI must be accessible through the Windows firewall, and for workgroup computers a registry key must be created to enable remote administrative actions under User Account Control (UAC). See Client Configuration for more details.
Step 5: Enter a MAK Key
Note: Since VAMT is not being run from a computer with internet access, clicking on Refresh Remaining Count will not operate. This function can only be performed using VAMT on a computer with Internet access.
Step 6: Use MAK Proxy Activation to install a MAK on computers in the Isolated LAB
Note: Selecting the Install MAK (overwrite existing) checkbox will force installation of the MAK. This must be done with care. If the computer has run for more than 30 days, then its Initial Grace period has expired and it will be put into Reduced Functionality Mode (RFM) if MAK Independent Activation is not completed successfully before the next logon. VAMT can be used to recover properly configured remote computers from RFM as long as they are accessible on the network.
Step 7: Save the CIL
In this step, the full CIL is saved on the local VAMT host. In MAK Proxy Activation, it is critical to retain this file. VAMT uses this information to apply the CIDs to the proper computers in Step 10, below
Step 8: Export the CIL
As stated above, the Security Policy for this Isolated Lab requires that no PII (Personally Identifiable Information) can be transferred from the Isolated Lab. A secure export should be performed to ensure that only product activation related information is stored in the CIL file to be transferred to the Core Network.
Note: Checking the Exclude any sensitive environment data checkbox excludes all Personally Identifiable Information (PII) from being saved in the CIL. Because of this, the CIL must be re-imported in this VAMT host and into the Full Save CIL file, so the CIDs requested from Microsoft (below) can be correctly assigned to the computers in the Isolated Lab Group. For more information on which fields are preserved in a secure export see Contents of the CIL (Computer Information List) in the VAMT.CHM file.
Step 9: Import the CIL on a VAMT Host with Internet Access
Step 10: Use MAK Proxy Activation to request CIDs (Confirmation IDs) from Microsoft
Step 11: Save the CIL from the Internet Connected VAMT Host
Step 12: Import the CIL on the original VAMT host within the Isolated Lab
Note: Saving a file that combined IID and CID is important in reimaging scenarios as described in Step 14.
Step 13: Use MAK Proxy Activation to Apply the CIDs and Activate the Isolated Computers
Step 14: Reimaging Scenario for Isolated Labs (OPTIONAL)
If the computers in the Isolated Lab have been reimaged and the underlying hardware has remained the same, the computers can use the existing IsolatedLabGroupwithCID.CIL file for activation. It is strongly recommended to back up this file and to protect it from being overwritten.
Note: Selecting the Install MAK (overwrite existing) checkbox will force installation of the MAK. This must be done with care. If the computer has run for more than 30 days, then its Initial Grace period has expired and it will be put into Reduced Functionality Mode (RFM) if the system is not activated successfully before the next logon. VAMT can be used to recover properly configured remote computers from RFM as long as they are accessible on the network.
This section describes the configuration changes required on all client computers to enable the VAMT tool to function correctly. An exception must be set in the client firewall. For computers in a workgroup, a registry key must be created and set properly or User Access Control (UAC) will not allow remote administrative operations.
In organizations where VAMT will be widely used may benefit from having these changes inside the master client image for Windows Vista or Windows Server codename "Longhorn".
Configure Windows Firewall to allow VAMT Access
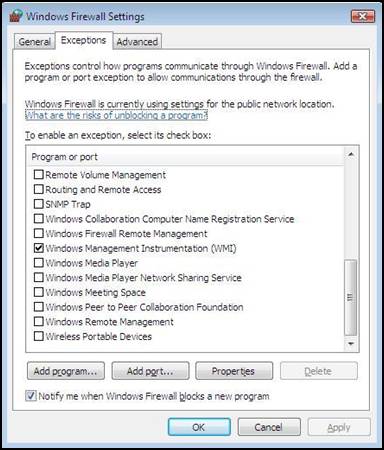
Figure 2: WMI firewall exception
Note: By default Windows Firewall Exceptions only apply to traffic originating on the local subnet. To expand the exception to apply to multiple subnets, you need to change the exception settings in the Windows Firewall with Advanced Security as shown below.
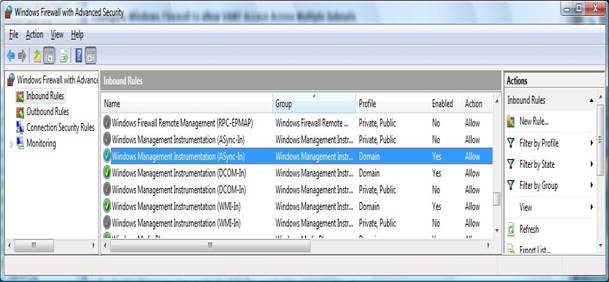
Figure 3: Windows Firewall with Advanced Security
Configure Windows Firewall to allow VAMT Access across Multiple Subnets
In Control Panel, double-click System and Maintenance, then Administrative Tools, and then Windows Firewall with Advanced Security.
Select "Inbound Rules" on the Left Pane
For each of the following three WMI items, for the applicable Network Profile (Domain, Public, Private), make the changes (A-C) :
A) Windows Management Instrumentation (ASync-In)
B) Windows Management Instrumentation (DCOM-In)
C) Windows Management Instrumentation (WMI-In)
On the General tab, select the "Allow the connections" checkbox.
On the Scope tab, change the Remote IP Address setting from "Local Subnet" (default) to allow the specific access you need.
On the Advanced tab, verify selection of all profiles that are applicable to the network. (Domain or Private/Public).
In certain scenarios, only a limited set of TCPIP ports are allowed through a hardware firewall. Administrators need to ensure that WMI (which relies on RPC over TCPIP) is allowed through these types of firewalls. By default the WMI port is a dynamically allocated random port above 1024. The following Microsoft knowledge article discusses how administrators can limit the range of dynamically allocated ports. This is useful if for example, the hardware firewall only allows traffic in a certain range of ports.
How to configure RPC dynamic port allocation to work with firewalls: https://support.microsoft.com/kb/154596
Create a Registry Value for VAMT to Operate against Workgroup Computers
Value Name: LocalAccountTokenFilterPolicy
Type: DWORD
Value Data: 1
Important: This section contains information about how to modify the registry. Make sure to back up the registry before you modify it. Make sure that you know how to restore the registry if a problem occurs. For more information about how to back up, restore, and modify the registry, click the following article number to view the article in the Microsoft Knowledge Base: Description of the Microsoft Windows registry.
Note: To discover Windows Vista computers in workgroups you must enable network discovery on the client.
Client Configuration Deployment Options
There are several options for organizations to easily configure the WMI firewall exception for computers:
Administrators need to be aware that the above configurations will open an additional port through the Windows Firewall on target computers and should be performed on computers that are protected by a network firewall. The WMI exception can be disabled (recommended) once each computer has been activated successfully.
Volume Activation Management Tool Privacy Statement
Last updated: February 2007
Microsoft is committed to protecting customer privacy. This privacy statement explains the data collection and use practices of the Microsoft Volume Activation Management Tool. This statement does not apply to other online or offline Microsoft sites, products, or services.
Activation is aimed at reducing software counterfeiting, thereby helping to ensure that Microsoft customers receive the software quality they expect. Once the software is activated, a specific product key becomes associated with the computer (the hardware) on which the software is installed. This association prevents the product key from being used to activate the same copy of the software on multiple computers. Changes to computer components or the software may require reactivation of the software
The Volume Activation Management Tool (VAMT) activates network-connected volume licensed computers. VAMT also supports scenarios in which client computers are isolated from the Internet as well as providing centralized management for MAK activation.
Collection of Information
During activation, product key information is sent to Microsoft along with a hardware hash, which is a non-unique number generated from the computer's hardware configuration. The hardware hash does not represent any personal information or information about the software. The hardware hash cannot be used to determine the make or model of the computer and it cannot be backward calculated to determine any additional information about the computer.
In addition, some standard information about the VAMT host will also be sent during activation. Standard computer information generally includes certain information about the computer software and hardware including IP address, operating system version, browser version, a code that identifies the computer's manufacturer and the regional and language settings.
Use of Information
Microsoft uses the information to confirm that a licensed copy of the software is being activated, and then it is aggregated for statistical analysis. Microsoft does not use the information to identify or contact any customer.
Information that is collected by or sent to
Microsoft may be stored and processed in the
Choice and Control
Activation is mandatory and must be completed within a predefined grace period. If you choose not to activate the software, you cannot use it after the grace period expires. If the software is not correctly licensed, you will not be able to activate it.
Changes to this Statement
Microsoft may occasionally update this privacy statement. When we do, we will also revise the "last updated" date at the top of the privacy statement. We encourage you to periodically review this privacy statement to stay informed about how we are helping to protect the information we collect.
Contact Information
Microsoft welcomes your comments regarding this privacy statement. If you believe that Microsoft has not adhered to this statement, please contact us electronically by clicking here , and we will use commercially reasonable efforts to promptly determine and remedy the problem.
Microsoft Privacy
Microsoft Corporation
The Windows Vista Volume Activation 2.0 Step-By-Step Guide is essential reading and a prerequisite for understanding the Volume Activation Management Tool Step-By-Step Guide. It is available at https://www.microsoft.com/technet/windowsvista/plan/volact1.mspx
Download Technical Documentation and Other Supporting Materials https://go.microsoft.com/fwlink/?LinkID=75674
For answers to frequently asked questions about Windows Vista Volume Activation 2.0, refer to the "Volume Activation 2.0 FAQ" in https://www.microsoft.com/technet/windowsvista/plan/faq.mspx
For information about the Microsoft Solution Accelerator for Business Desktop Deployment (BDD): https://www.microsoft.com/technet/desktopdeployment/bdd/2007/default.mspx
For a list of Volume License products available, go to:
|