The MIT Guide to Lock Picking
Lockpicking Secrets
Bumping locks
Safe Locks Safecracking for the computer scientist
Illustrated Secrets of Lockpicking
Cryptology and Physical Security Wired -The Lock Busters
Locksmithing
Cutaway
The Lock Pick Guide
Lock Picking & Lock-Smith Secret 17517l111r s
Beginner to Advanced

The Ancient Egyptians were the first to come up with a complicated security device.
This was the pin tumbler lock.
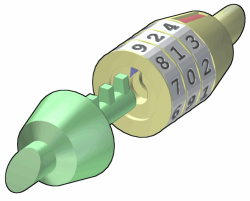
We use the same security principle today on millions of applications. The most commonly used lock today is the pin tumbler lock. A series of pins that are divided at certain points must be raised to these dividing points in relationship to the separation between the cylinder wall and the shell of the lock by a key cut for that particular series of pin divisions. Thus the cylinder can be turned, and the mechanism or lock is unlocked.
The MIT Guide to Lock Picking
1 It's Easy
2 How a Key Opens a Lock
3 The Flatland Model
4 Basic Picking & The Binding Defect
5 The Pin Column Model
6 Basic Scrubbing
7 Advanced Lock Picking
7.1 Mechanical Skills
7.2 Zen and the Art of Lock Picking
7.3 Analytic Thinking
8 Exercises
8.1 Exercise 1: Bouncing the pick
8.2 Exercise 2: Picking pressure
8.3 Exercise 3: Picking Torque
8.4 Exercise 4: Identifying Set Pins
8.5 Exercise 5: Projection
9 Recognizing and Exploiting Personality Traits
9.1 Which Way to Turn
9.2 How Far to
Turn
9.3 Gravity
9.4 Pins Not Setting
9.5 Elastic Deformation
9.6 Loose Plug
9.7 Pin Diameter
9.8 Beveled Holes and Rounded pins
9.9 Mushroom Friver Pins
9.10 Master Keys
9.11 Driver or Spacer Enters Keyway
9.12 Vibration Picking
9.13 Disk Tumblers
10 Final Remarks
A Tools
A.1 Pick
A.2 Street
A.3 Bicycle spokes
A.4 Brick Strap
B Legal Issues
Secrets of Lockpicking

Tools
Lock Identification
Pin Tumbler Locks
Wafer Tumbler Locks
Double Wafer Locks
Pin and Wafer Tumbler Padlocks
Tubular Cylinder Locks
Mushroom and Spool Pin Tumbler Locks
Magnetic Locks
Disk Tumbler Locks
Tips for Success
Bumping locks 
In this paper we describe an underestimated lock-opening technique by which a large variety of mechanical locks can be opened quickly and without damage by a relatively untrained attacker.
Among other things we examine how this works, why it works better on some locks than on others, whether one could detect that this technique was used against a lock and what the lock-industry could do to protect new locks against this technique.
Understanding the threat of this new method of manipulating locks is added importance because we have found that this method actually works better on
the more expensive mechanical locks generally considered
to be most resistant to manipulation.
Safe Locks Safecracking for the
Computer Scientist

This paper is a general survey of safe and vault security from a
computer science perspective, with emphasis on the metrics used to
evaluate these systems and the weaknesses that cause them to fail.
We examine security against forced, covert and surreptitious
safe opening, focusing on the mechanical combination locks most
commonly used
on commercial safes in the
Our analysis contrasts the philosophy and tools of physical security
with those of information security, especially where
techniques might be
profitably applied across these disciplines.
Cryptology and Physical Security
This paper examines mechanical lock security from the perspective of
computer science and cryptology.
We focus on new and practical attacks for amplifying rights in mechanical pin tumbler locks.
Given access to a single master-keyed lock and its associated key,
a procedure is given that allows discovery and creation of a working master key for the system.
No special skill or equipment, beyond a small number of blank keys and a metal file, is required and the attacker need engage in no suspicious behavior at the lock's location.
Countermeasures are also described that may provide limited protection under certain circumstances. We conclude with directions for research in this area
and the suggestion that mechanical locks are worthy objects for study and scrutiny.
Wired -The Lock Busters
They've never met a padlock - or six -
pin
Live, from the lock-picking championship of the world.
The Lock Pick Guide
What are "pick guns" or "automatic pickers"
and do they work?
Where can I get a lock pick set?
How do I open a Kryptonite lock?
How can I get keys stamped
"DO NOT DUPLICATE" duplicated?
What should I do next after I read the ebook?
How do I continue learning about Locksmithing?
How do I learn the Locksmithing trade?
Is there a formula that can find the
combination of a Master Lock?
What is "impressioning"?
What is code? What is codebook?
How do I open a car door with a Slim Jim?
I have a safe without the combination - how do I open it?

11 EBOOKS IN PDF FORMAT

Free 28 Links to Websites with Video!
Watch while the experts talk you thru step by step

Free 1 Hr video on Lockpicking Windows Media Player)
Learn all you ever wanted to know about the art of Lockpicking & Locksmithing!
|