Most RIS server security issues are addressed in "Planning RIS Server Security" (ACIRIS_05.doc) on the Windows Server 2003 Deployment Kit companion CD (or see "Planning RIS Server Security" on the Web at https://www.microsoft.com/reskit). The security des 424f57e ign issue details that must now be completed include choosing how to do the following:
Provide secure responses from your RIS server to clients, with load balancing.
Provide security for non-prestaged RIS clients.
Optimize network security for RIS services.
Provide authorization for your RIS servers.
To control how a RIS server responds to remote boot-enabled clients that request service, set Client support options on the RIS server Properties dialog box. Available settings consist of the following:
Respond to client computers requesting service. The RIS server responds to all clients requesting service. This is the least secure setting because the RIS server does not distinguish between authorized and unauthorized clients.
Do not respond to unknown client computers. The RIS server only responds to clients that have a prestaged computer account object in Active Directory. This is the most secure setting for your network because it enables you to limit access to only authorized clients that are prestaged in Active Directory.
If you configure a RIS server with the Respond to all clients requesting service option, you designate that server to handle all client requests for RIS services. In this configuration, you have less security with respect to unknown and possibly unauthorized clients accessing the RIS server. However, you can enhance security by configuring the RIS server to only respond to prestaged clients using the Do not respond to unknown client computers option.
In addition, if you prestage all computer accounts and use the RIS referral and install server configuration described in "Designing the RIS Network Deployment Configuration," you can provide load balancing for client service requests by:
Dedicating RIS servers as referral servers that acknowledge all initial prestaged client service requests and then provide referrals to the appropriate RIS install servers.
Using specific RIS install servers to handle service requests from designated clients.
Figure . illustrates how a referral server responds to non-prestaged and prestaged RIS clients.
Figure . Securing Client Request Responses and Achieving Load Balancing With RIS Servers
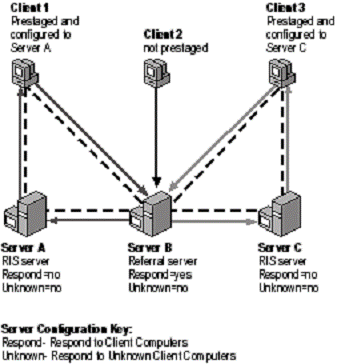
In Figure . , only Server B is configured as a referral server because it is the only one that can respond to initial client requests for RIS services. It is also configured to only respond to prestaged or "known" clients. Because Client 1 and Client 3 are prestaged and configured to obtain service from a specific RIS server, they receive replies from Server B that refer them to either Server A or Server C.
In Figure . , Servers A and C cannot reply to initial client service requests, but only provide operating system installation services to Client 1 and Client 3 through referrals from Server B. Client 2 is not recognized by Server B because it is not prestaged and therefore cannot receive service from any RIS server.
If you configure Server B to not use the Do not respond to unknown client computers option, then Server B itself replies to service requests from Client 2 and offers itself as the remote boot server. Server B functions this way because it is configured to respond to all clients requesting service (Respond = Yes in Figure . ).
If you have not already done so, use the "RIS Server Properties" and "RIS Network Deployment Configuration" sections of job aid "Designing the RIS Server Configuration" (ACIRIS_09.doc) on the Windows Server 2003 Deployment Kit companion CD (or see "Designing the RIS Server Configuration" on the Web at https://www.microsoft.com/reskit) to record the Client support options you choose and whether you want to use the RIS referral and install server configuration.
To improve the security of non-prestaged RIS clients, you can control which valid users can create computer accounts in Active Directory during installation. You do this by using the Active Directory Delegation feature to preassign the right to join computers to the domain. This automatically provides the user with the Create/Delete Computer Objects permission. You can also do this by explicitly adding the Create Computer Objects and Delete Computer Objects permissions to the user within the Computers container of the appropriate domain or organizational unit in Active Directory.
By pre-assigning prestaged client computers with the right to join a domain, you enable users to turn on their systems, connect to a RIS server, log on with their domain accounts, and perform an unassisted installation of an operating system image - all without compromising the security of your network.
For this part of your RIS server security design process, use the "RIS Server Security" section of job aid "Designing the RIS Server Configuration" (ACIRIS_09.doc) on the Windows Server 2003 Deployment Kit companion CD (or see "Designing the RIS Server Configuration" on the Web at https://www.microsoft.com/reskit) to indicate whether you want to secure non-prestaged RIS clients by giving them the right to join a domain using the Active Directory Delegation feature.
You can optimize RIS server security by using prestaged clients. After you prestage computer accounts in Active Directory, configure your RIS server to only respond to these prestaged clients. To further enhance security, you can configure your users with read, write, and reset or change password permissions on the prestaged computer account objects.
For this part of your RIS server security design process, use the "RIS Server Security" section of job aid "Designing the RIS Server Configuration" (ACIRIS_09.doc) on the Windows Server 2003 Deployment Kit companion CD (or see "Designing the RIS Server Configuration" on the Web at https://www.microsoft.com/reskit) to record your decision to enhance the security of prestaged clients by setting user permissions on the prestaged computer accounts. Also indicate the user groups you want to receive these permissions.
To ensure that your RIS clients are serviced by known RIS servers on the network, you must authorize each RIS server. This ensures that the RIS server is recognized in Active Directory.
The easiest way to authorize RIS on a computer running Windows Server 2003 is to use the Verify Server feature on the Remote Install tab of the RIS server Properties dialog box. You can also type the following command at the command line:
Risetup /Check
If you intend to delegate this task to specific personnel, they must be part of the Enterprise Admins security group or another group that you configure with this permission in order to access and configure a RIS server.
Alternatively, you can authorize a RIS server to Active Directory by using the Authorize function in the Manage Authorized Servers dialog box in the Windows Server 2003, Windows XP, or Windows 2000 DHCP snap-in.
To use the DHCP snap-in to authorize the RIS server, it is unnecessary to install the DHCP service. You can use this snap-in if the Administrative Tools package is installed on a computer running Windows XP Professional or Windows Server 2003, from which you can authorize the RIS server. You can install this package by running the adminpak.msi installer - located in the System32 directory of a computer running Windows Server 2003 - on the computer running Windows XP Professional.
You should not attempt to install Windows Server 2003 DHCP on a RIS server just to obtain the snap-in. To service RIS clients, any combined Windows Server 2003 DHCP/RIS server must have a fully functional DHCP service with defined and active scopes. This is because the Windows Server 2003 DHCP service on a combined server is aware that RIS is also present. If a client requests DHCP and remote boot services in its DHCP discovery broadcast, DHCP issues a single reply containing the specific details on DHCP and remote booting for that server. If the Windows Server 2003 DHCP service is not answering clients properly, the server does not generate a remote boot reply to clients requesting service.
For this part of your RIS server security design process use the "RIS Server Security" section of job aid "Designing the RIS Server Configuration" (ACIRIS_09.doc) on the Windows Server 2003 Deployment Kit companion CD (or see "Designing the RIS Server Configuration" on the Web at https://www.microsoft.com/reskit) to record the following information:
The names of RIS server authorization personnel, who are either included in the Enterprise Admins group or in a separate RIS authorizers group that has appropriate permissions.
The RIS server authorization location.
The RIS server authorization method.
Whether you need to install the Administrative Tools package on a computer running Windows XP Professional.
If you have multiple RIS servers, you might simplify things by using a common location and authorization method for each one. For example, you can choose to authorize all RIS servers from a remote administration session by using the Verify button in RIS server Properties.
|