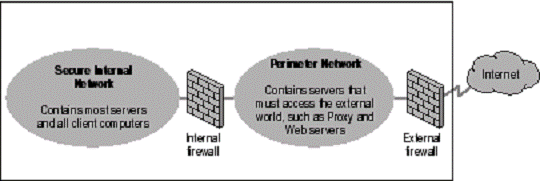
A perimeter network protects your intranet or enterprise LAN from intrusion by controlling access from the Internet or other large network. The perimeter network (also known as a demilitarized zone or DMZ) is bounded by firewalls. A firewall is not a single compon 959o1423j ent, but rather a system or combination of systems that enforces a boundary between two or more networks.
Figure 1.11 shows a perimeter network bounded by firewalls placed between a private network and the Internet in order to secure the private network.
Figure 1. Perimeter Network Securing an Internal Network
Organizations vary in their use of firewalls for providing security. IP packet filtering offers weak security, is cumbersome to manage, and is easily defeated. Application gateways are more secure than packet filters and easier to manage because they pertain only to a few specific applications, such as a particular e-mail system. Circuit gateways are most effective when the user of a network application is of greater concern than the data being passed by that application. The proxy server - the recommended solution - is a comprehensive security tool that includes an application gateway, safe access for anonymous users, and other services.
IP packet filtering |
You can configure packet filtering, the earliest implementation of firewall technology, to accept or deny specific types of packets. Packet headers are examined for source and destination addresses, TCP and UDP port numbers, and other information. Packet filtering is a limited technology that works best in clear security environments where, for example, everything outside the perimeter network is not trusted and everything inside is. You cannot use IP packet filtering when IP packet payloads are encrypted because the port numbers are encrypted and therefore cannot be examined.
In recent years, various vendors have improved on the packet filtering method by adding intelligent decision-making features to the packet-filtering core, thus creating a new form of packet filtering called stateful protocol inspection.
Application gateways |
Used when the actual content of an application is of greatest concern, application gateways do not adapt easily to changes in technology. However, unlike IP packet filtering, application gateways can be used in conjunction with encryption.
Circuit gateways |
As tunnels connecting specific processes or systems on each side of a firewall, circuit gateways are best employed in situations where the person using an application is potentially a greater risk than the information that the application carries. The circuit gateway differs from a packet filter in its capability for connecting to an out-of-band application scheme that can add additional information.
Proxy servers |
Proxy servers are comprehensive security tools that include firewall and application gateway functionality to manage Internet traffic to and from a private intranet. Proxy servers also provide document caching and access control. A proxy server can improve performance by caching and directly supplying frequently requested data such as a popular Web page. A proxy server also can filter and discard requests that the owner does not consider appropriate, such as requests for unauthorized access to proprietary files.
Take advantage of those firewall security features that can help you. Position a perimeter network in your network topology at a point where all traffic from outside the corporate network must pass through the perimeter that the external firewall maintains. You can fine-tune access control for the firewall to meet your needs and can configure firewalls to report all attempts at unauthorized access.
Availability refers to how much time the network is operational. Planning well for availability improves both your network's mean time between failures (MTBF) and its mean time to recovery (MTTR) after a network failure.
To improve availability in your IP network design, you must know your organization's availability requirements. For some organizations, unanticipated down time is simply an irritating inconvenience. In other environments, unanticipated down time could mean financial disaster, drastic loss of credibility, or, as in health care or law enforcement, a risk to safety.
Figure 1.12 shows the process for improving availability on your network.
Figure 1. Improving Availability
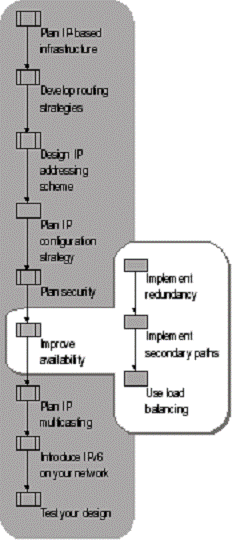
Each method for improving availability places different demands on the design of your network. As the risk of down time to your operation increases, build more redundancy into your design, both in hardware and routing. Similarly, as the consequences of failure increase, make your network more resilient by increasing the amount of stress it can handle before it loses functionality.
Single points of failure, such as devices, links, and interfaces, can make a network vulnerable. If one such point fails, it isolates users from services and, in the worst case, causes entire sections of the network to fail. For a purely hierarchical network - one based on summarization and controlled access between tiers - every device and link is a point of failure.
Redundancy provides alternative paths around points of failure. In a purely redundant network, each individual device, link, and interface is dispensable. No single device, link, or interface can isolate users or cause the network to fail.
In most production environments, neither a purely hierarchical nor a purely redundant network is practical. You must balance the efficiency of a hierarchical network with the safety net of redundancy.
After deploying multiple devices to eliminate single points of failure, configure secondary paths to take advantage of the multiple devices. A secondary path, or backup path, consists of the interconnecting devices and the links between them that duplicate the devices and links in the primary path. For example, you can configure multiple routers to provide redundancy.
A redundant design uses the secondary path to maintain network connectivity when any of the primary path's devices or links fails. Be sure to test any secondary paths on a regular basis. Do not assume that they will work. If possible, ensure that the switch from the primary path to the secondary path occurs transparently. For mission-critical applications, automatic failover is mandatory.
In addition to its safety net function, redundancy plays a second valuable role. By properly configuring two or more paths that connect the same source and destination networks, you can significantly improve throughput by providing load balancing. Load balancing evenly divides the flow of traffic among parallel links.
Most routing protocols based on open standards support load balancing across paths that the protocol determines to be equally favorable to the destination. In addition, some vendors' proprietary routing protocols support load balancing where the costs of the paths (their relative favorability to the destination in terms of shortest distance, number of hops, and other criteria) are not considered equal.
For more information about network load balancing, see "Designing Network Load Balancing" in Planning Server Deployments of this kit.
|